Backup/Server/Dokumentation/Anhänge: Unterschied zwischen den Versionen
K Textersetzung - „z. B. “ durch „beispielsweise “ |
|||
| (82 dazwischenliegende Versionen von 3 Benutzern werden nicht angezeigt) | |||
| Zeile 1: | Zeile 1: | ||
#Angebot interner Backup | #Angebot interner Backup/Server | ||
#Angebot externer Backup- | #Angebot externer Backup-Space | ||
#Kundenauftrag | #Kundenauftrag | ||
#Raumplan | #Raumplan | ||
| Zeile 8: | Zeile 8: | ||
#Config-Datei rsnapshot | #Config-Datei rsnapshot | ||
#Config-Datei duply | #Config-Datei duply | ||
#Ablauf | #Ablauf GnuPG: Schlüsselerstellung | ||
#Fotos | #Fotos | ||
#Messprotokolle | #Messprotokolle | ||
=rsnapshot.conf | = rsnapshot.conf = | ||
################################################# | ################################################# | ||
| Zeile 107: | Zeile 107: | ||
# BACKUP LEVELS / INTERVALS # | # BACKUP LEVELS / INTERVALS # | ||
# Must be unique and in ascending order # | # Must be unique and in ascending order # | ||
# e.g. alpha, beta, gamma, | # e.g. alpha, beta, gamma, und weitere # | ||
######################################### | ######################################### | ||
| Zeile 272: | Zeile 272: | ||
#backup rsync://rsync.samba.org/rsyncftp/ rsync.samba.org/rsyncftp/ | #backup rsync://rsync.samba.org/rsyncftp/ rsync.samba.org/rsyncftp/ | ||
=duply.conf | = duply.conf = | ||
# gpg encryption settings, simple settings: | # gpg encryption settings, simple settings: | ||
# | # GnuPG_KEY='disabled' - disables encryption alltogether | ||
# | # GnuPG_KEY='<key1>[,<key2>]'; GnuPG_PW='pass' - encrypt with keys, | ||
# sign if secret key of key1 is available use | # sign if secret key of key1 is available use GnuPG_PW for sign & decrypt | ||
# Note: you can specify keys via all methods described in gpg manpage, | # Note: you can specify keys via all methods described in gpg manpage, | ||
# section "How to specify a user ID", escape commas (,) via backslash (\) | # section "How to specify a user ID", escape commas (,) via backslash (\) | ||
# e.g. 'Mueller, Horst', 'Bernd' -> 'Mueller\, Horst, Bernd' | # e.g. 'Mueller, Horst', 'Bernd' -> 'Mueller\, Horst, Bernd' | ||
# as they are used to separate the entries | # as they are used to separate the entries | ||
# | # GnuPG_PW='passphrase' - symmetric encryption using passphrase only | ||
''' | '''GnuPG_KEY='B2E20485FF7FC772 ' ''' | ||
''' | '''GnuPG_PW='roottutgut' ''' | ||
# gpg encryption settings in detail (extended settings) | # gpg encryption settings in detail (extended settings) | ||
# the above settings translate to the following more specific settings | # the above settings translate to the following more specific settings | ||
# | # GnuPG_KEYS_ENC='<keyid1>[,<keyid2>,...]' - list of pubkeys to encrypt to | ||
# | # GnuPG_KEY_SIGN='<keyid1>|disabled' - a secret key for signing | ||
# | # GnuPG_PW='<passphrase>' - needed for signing, decryption and symmetric | ||
# encryption. If you want to deliver different passphrases for e.g. | # encryption. If you want to deliver different passphrases for e.g. | ||
# several keys or symmetric encryption plus key signing you can use | # several keys or symmetric encryption plus key signing you can use | ||
# gpg-agent. Simply make sure that | # gpg-agent. Simply make sure that GnuPG_AGENT_INFO is set in environment. | ||
# also see "A NOTE ON SYMMETRIC ENCRYPTION AND SIGNING" in duplicity manpage | # also see "A NOTE ON SYMMETRIC ENCRYPTION AND SIGNING" in duplicity manpage | ||
# notes on en/decryption | # notes on en/decryption | ||
| Zeile 299: | Zeile 299: | ||
# for security reasons it makes sense to separate the signing key from the | # for security reasons it makes sense to separate the signing key from the | ||
# encryption keys. https://answers.launchpad.net/duplicity/+question/107216 | # encryption keys. https://answers.launchpad.net/duplicity/+question/107216 | ||
# | #GnuPG_KEYS_ENC='<pubkey1>,<pubkey2>,...' | ||
# | #GnuPG_KEY_SIGN='<prvkey>' | ||
# set if signing key passphrase differs from encryption (key) passphrase | # set if signing key passphrase differs from encryption (key) passphrase | ||
# NOTE: available since duplicity 0.6.14, translates to SIGN_PASSPHRASE | # NOTE: available since duplicity 0.6.14, translates to SIGN_PASSPHRASE | ||
# | #GnuPG_PW_SIGN='<signpass>' | ||
# uncomment and set a file path or name force duply to use this gpg executable | # uncomment and set a file path or name force duply to use this gpg executable | ||
# available in duplicity 0.7.04 and above (currently unreleased 06/2015) | # available in duplicity 0.7.04 and above (currently unreleased 06/2015) | ||
# | #GnuPG='/usr/local/gpg-2.1/bin/gpg' | ||
# gpg options passed from duplicity to gpg process (default='') | # gpg options passed from duplicity to gpg process (default='') | ||
| Zeile 314: | Zeile 314: | ||
# or "--personal-cipher-preferences AES256,AES192,AES..." | # or "--personal-cipher-preferences AES256,AES192,AES..." | ||
# or "--homedir ~/.duply" - keep keyring and gpg settings duply specific | # or "--homedir ~/.duply" - keep keyring and gpg settings duply specific | ||
# or "--pinentry-mode loopback" - needed for | # or "--pinentry-mode loopback" - needed for GnuPG 2.1+ _and_ | ||
# also enable allow-loopback-pinentry in your .gnupg/gpg-agent.conf | # also enable allow-loopback-pinentry in your .gnupg/gpg-agent.conf | ||
''' | '''GnuPG_OPTS='--compress-algo=bzip2 --bzip2-compress-level=9 --personal- cipher-preferences AES256' ''' | ||
# disable preliminary tests with the following setting | # disable preliminary tests with the following setting | ||
# | #GnuPG_TEST='disabled' | ||
# backend, credentials & location of the backup target (URL-Format) | # backend, credentials & location of the backup target (URL-Format) | ||
| Zeile 327: | Zeile 327: | ||
# sftp://bob:secret@backupserver.com//home/bob/dupbkp | # sftp://bob:secret@backupserver.com//home/bob/dupbkp | ||
# for details and available backends see duplicity manpage, section URL Format | # for details and available backends see duplicity manpage, section URL Format | ||
# | # https://duplicity.nongnu.org/duplicity.1.html#sect7 | ||
# BE AWARE: | # BE AWARE: | ||
# some backends (cloudfiles, S3 | # some backends (cloudfiles, S3 und weitere) need additional env vars to be set to | ||
# work properly, read after the TARGET definition for more details. | # work properly, read after the TARGET definition for more details. | ||
# ATTENTION: | # ATTENTION: | ||
# characters other than A-Za-z0-9.-_.~ in the URL have to be | # characters other than A-Za-z0-9.-_.~ in the URL have to be | ||
# replaced by their url encoded pendants, see | # replaced by their url encoded pendants, see | ||
# | # https://en.wikipedia.org/wiki/Url_encoding | ||
# if you define the credentials as TARGET_USER, TARGET_PASS below duply | # if you define the credentials as TARGET_USER, TARGET_PASS below duply | ||
# will try to url_encode them for you if the need arises. | # will try to url_encode them for you if the need arises. | ||
| Zeile 444: | Zeile 444: | ||
#DUPL_PARAMS="$DUPL_PARAMS --put_your_options_here " | #DUPL_PARAMS="$DUPL_PARAMS --put_your_options_here " | ||
== | ==Konfiguration exclude-Datei== | ||
# vi /root/.duply/backuptest/exclude | # vi /root/.duply/backuptest/exclude | ||
| Zeile 455: | Zeile 455: | ||
# - ** | # - ** | ||
# for more details see duplicity manpage, section File Selection | # for more details see duplicity manpage, section File Selection | ||
# | # https://duplicity.nongnu.org/duplicity.1.html#sect9 | ||
'''+ /etc''' | '''+ /etc''' | ||
'''- **''' | '''- **''' | ||
== | ==Erstellung gpg-key== | ||
# gpg --full-generate-key | # gpg --full-generate-key | ||
gpg (GnuPG) 2.2.12; Copyright (C) 2018 Free Software Foundation, Inc. | gpg (GnuPG) 2.2.12; Copyright (C) 2018 Free Software Foundation, Inc. | ||
| Zeile 496: | Zeile 496: | ||
Ändern: (N)ame, (K)ommentar, (E)-Mail oder (F)ertig/(A)bbrechen? F | Ändern: (N)ame, (K)ommentar, (E)-Mail oder (F)ertig/(A)bbrechen? F | ||
Wir müssen eine ganze Menge Zufallswerte erzeugen. Sie können dies | Wir müssen eine ganze Menge Zufallswerte erzeugen. Sie können dies | ||
unterstützen, indem Sie | unterstützen, indem Sie beispielsweise in einem anderen Fenster/Konsole irgendetwas | ||
tippen, die Maus verwenden oder irgendwelche anderen Programme benutzen. | tippen, die Maus verwenden oder irgendwelche anderen Programme benutzen. | ||
Wir müssen eine ganze Menge Zufallswerte erzeugen. Sie können dies | Wir müssen eine ganze Menge Zufallswerte erzeugen. Sie können dies | ||
unterstützen, indem Sie | unterstützen, indem Sie beispielsweise in einem anderen Fenster/Konsole irgendetwas | ||
tippen, die Maus verwenden oder irgendwelche anderen Programme benutzen. | tippen, die Maus verwenden oder irgendwelche anderen Programme benutzen. | ||
gpg: /root/.gnupg/trustdb.gpg: trust-db erzeugt | gpg: /root/.gnupg/trustdb.gpg: trust-db erzeugt | ||
| Zeile 532: | Zeile 532: | ||
--------------------------- --> | --------------------------- --> | ||
== | |||
Befehl | == Passphrase kann nicht abgefragt werden == | ||
=== Befehl === | |||
# duply /root/.duply/Name_Backup_Profil full | # duply /root/.duply/Name_Backup_Profil full | ||
Meldung | === Meldung === | ||
[GNUPG:] PINENTRY_LAUNCHED 23758 curses 1.1.0 - linux - | [GNUPG:] PINENTRY_LAUNCHED 23758 curses 1.1.0 - linux - | ||
gpg: Beglaubigung fehlgeschlagen: Unpassender IOCTL (I/O-Control) für das Gerät | gpg: Beglaubigung fehlgeschlagen: Unpassender IOCTL (I/O-Control) für das Gerät | ||
| Zeile 543: | Zeile 544: | ||
gpg: /usr/bin/duply: sign+encrypt failed: Unpassender IOCTL (I/O-Control) für das Gerät | gpg: /usr/bin/duply: sign+encrypt failed: Unpassender IOCTL (I/O-Control) für das Gerät | ||
Lösung | === Lösung === | ||
echo use-agent >> ~/.gnupg/gpg.conf | echo use-agent >> ~/.gnupg/gpg.conf | ||
echo "pinentry-mode loopback" >> ~/.gnupg/gpg.conf | echo "pinentry-mode loopback" >> ~/.gnupg/gpg.conf | ||
echo allow-loopback-pinentry >> ~/.gnupg/gpg-agent.conf | echo allow-loopback-pinentry >> ~/.gnupg/gpg-agent.conf | ||
Hintergrund | === Hintergrund === | ||
* Es kommt zu dieser Fehlermeldung, weil gpg die Passphrase nicht automatisch abfragen konnte. | |||
* Die erledigt der gpg-agent, der wiederum [[pinentry-curses|pinentry-curses]] zur sicheren Übertragung der Passphrase vewendet. | |||
* In der gpg.conf muss angegeben werden, dass der gpg-agent verwendet werden soll (use-agent). | |||
* Und in welchem Modus dieser verwendet werden soll (pinentry-mode loopback). | |||
* In der gpg-agent.conf muss dem gpg-agent erlaubt werden den loop-back-pinentry durchzuführen (allow-loopback-pinentry). | |||
| Zeile 619: | Zeile 620: | ||
----------------------------- --> | ----------------------------- --> | ||
== | ==Privater ssh-key (RSA) nicht valide== | ||
Befehl | === Befehl === | ||
# duply /root/.duply/Name_Backup_Profil full | # duply /root/.duply/Name_Backup_Profil full | ||
Meldung | === Meldung === | ||
# duply /root/.duply/ersatzBU/ full | # duply /root/.duply/ersatzBU/ full | ||
Start duply v2.1, time is 2020-11-10 12:17:27. | Start duply v2.1, time is 2020-11-10 12:17:27. | ||
Using profile '/root/.duply/ersatzBU'. | Using profile '/root/.duply/ersatzBU'. | ||
Using installed duplicity version 0.7.18.2, python 2.7.16 (/usr/bin/python2), gpg 2.2.12 (Home: /root/.gnupg), awk 'GNU Awk 4.2.1, API: 2.0 (GNU MPFR 4.0.2, GNU MP 6.1.2)', grep 'grep (GNU grep) 3.3', bash '5.0.3(1)-release (x86_64-pc-linux-gnu)'. | Using installed duplicity version 0.7.18.2, python 2.7.16 (/usr/bin/python2), gpg 2.2.12 (Home: /root/.gnupg), awk 'GNU Awk 4.2.1, API: 2.0 (GNU MPFR 4.0.2, GNU MP 6.1.2)', grep 'grep (GNU grep) 3.3', bash '5.0.3(1)-release (x86_64-pc-linux-gnu)'. | ||
Autoset found secret key of first | Autoset found secret key of first GnuPG_KEY entry '1A955E6287B8E312' for signing. | ||
Checking TEMP_DIR '/tmp' is a folder and writable (OK) | Checking TEMP_DIR '/tmp' is a folder and writable (OK) | ||
Test - Encrypt to '1A955E6287B8E312' & Sign with '1A955E6287B8E312' (OK) | Test - Encrypt to '1A955E6287B8E312' & Sign with '1A955E6287B8E312' (OK) | ||
| Zeile 640: | Zeile 641: | ||
'''Write file 'gpgkey.1A955E6287B8E312.sec.asc' (OK)''' | '''Write file 'gpgkey.1A955E6287B8E312.sec.asc' (OK)''' | ||
=== INFO === | |||
'''duply exported new keys to your profile.''' | '''duply exported new keys to your profile.''' | ||
'''You should backup your changed profile folder now and store it in a safe place.''' | '''You should backup your changed profile folder now and store it in a safe place.''' | ||
--- Start running command FULL at 12:17:30.512 --- | --- Start running command FULL at 12:17:30.512 --- | ||
| Zeile 703: | Zeile 702: | ||
--- Finished state FAILED 'code 23' at 12:17:31.728 - Runtime 00:00:01.216 --- | --- Finished state FAILED 'code 23' at 12:17:31.728 - Runtime 00:00:01.216 --- | ||
Lösung | === Lösung === | ||
Benötigt duplicity den ssh-key im PEM-Format, wenn duplicity sich via ssh anmelden soll. - Verifiziert durch Duplizierung des Fehlers. | Benötigt duplicity den ssh-key im PEM-Format, wenn duplicity sich via ssh anmelden soll. - Verifiziert durch Duplizierung des Fehlers. | ||
# ssh-keygen -p -f /root/.ssh/id_rsa -m pem -P "" -N "" | # ssh-keygen -p -f /root/.ssh/id_rsa -m pem -P "" -N "" | ||
Änderung des Formats des ssh-Keys von OPENSSH zu PEM ([https://en.wikipedia.org/wiki/Privacy-Enhanced_Mail Privacy-Enhanced Mail]) | Änderung des Formats des ssh-Keys von OPENSSH zu PEM ([https://en.wikipedia.org/wiki/Privacy-Enhanced_Mail Privacy-Enhanced Mail]) | ||
ssh-keygen | |||
ssh-keygen | |||
{|class="wikitable" | {|class="wikitable" | ||
!Option !! Beschreibung | !Option !! Beschreibung | ||
| Zeile 729: | Zeile 725: | ||
Stellt die neue Passphrase bereit. | Stellt die neue Passphrase bereit. | ||
|- | |- | ||
|"Passphrase"|| Da hier weder im alten noch im neuen Format für den ssh-key eine Passphrase verwendet wurde bzw. werden soll, wird zwischen den beiden " nichts eingetragen: "" | |"Passphrase"|| Da hier weder im alten noch im neuen Format für den ssh-key eine Passphrase verwendet wurde bzw. werden soll, wird zwischen den beiden " nichts eingetragen: "" | ||
|} | |} | ||
| Zeile 739: | Zeile 735: | ||
Using profile '/root/.duply/ersatzBU'. | Using profile '/root/.duply/ersatzBU'. | ||
Using installed duplicity version 0.7.18.2, python 2.7.16 (/usr/bin/python2), gpg 2.2.12 (Home: /root/.gnupg), awk 'GNU Awk 4.2.1, API: 2.0 (GNU MPFR 4.0.2, GNU MP 6.1.2)', grep 'grep (GNU grep) 3.3', bash '5.0.3(1)-release (x86_64-pc-linux-gnu)'. | Using installed duplicity version 0.7.18.2, python 2.7.16 (/usr/bin/python2), gpg 2.2.12 (Home: /root/.gnupg), awk 'GNU Awk 4.2.1, API: 2.0 (GNU MPFR 4.0.2, GNU MP 6.1.2)', grep 'grep (GNU grep) 3.3', bash '5.0.3(1)-release (x86_64-pc-linux-gnu)'. | ||
Autoset found secret key of first | Autoset found secret key of first GnuPG_KEY entry '1A955E6287B8E312' for signing. | ||
Checking TEMP_DIR '/tmp' is a folder and writable (OK) | Checking TEMP_DIR '/tmp' is a folder and writable (OK) | ||
Test - Encrypt to '1A955E6287B8E312' & Sign with '1A955E6287B8E312' (OK) | Test - Encrypt to '1A955E6287B8E312' & Sign with '1A955E6287B8E312' (OK) | ||
| Zeile 839: | Zeile 835: | ||
--- Finished state OK at 12:39:21.932 - Runtime 00:00:03.379 --- | --- Finished state OK at 12:39:21.932 - Runtime 00:00:03.379 --- | ||
== | ==Von synchronen auf asynchronen Modus umstellen== | ||
*Arbeitet Backupvorgang effizienter ab. | *Arbeitet Backupvorgang effizienter ab. | ||
| Zeile 859: | Zeile 855: | ||
Using profile '/root/.duply/ersatzBU'. | Using profile '/root/.duply/ersatzBU'. | ||
Using installed duplicity version 0.7.18.2, python 2.7.16 (/usr/bin/python2), gpg 2.2.12 (Home: /root/.gnupg), awk 'GNU Awk 4.2.1, API: 2.0 (GNU MPFR 4.0.2, GNU MP 6.1.2)', grep 'grep (GNU grep) 3.3', bash '5.0.3(1)-release (x86_64-pc-linux-gnu)'. | Using installed duplicity version 0.7.18.2, python 2.7.16 (/usr/bin/python2), gpg 2.2.12 (Home: /root/.gnupg), awk 'GNU Awk 4.2.1, API: 2.0 (GNU MPFR 4.0.2, GNU MP 6.1.2)', grep 'grep (GNU grep) 3.3', bash '5.0.3(1)-release (x86_64-pc-linux-gnu)'. | ||
Autoset found secret key of first | Autoset found secret key of first GnuPG_KEY entry '1A955E6287B8E312' for signing. | ||
Checking TEMP_DIR '/tmp' is a folder and writable (OK) | Checking TEMP_DIR '/tmp' is a folder and writable (OK) | ||
Test - Encrypt to '1A955E6287B8E312' & Sign with '1A955E6287B8E312' (OK) | Test - Encrypt to '1A955E6287B8E312' & Sign with '1A955E6287B8E312' (OK) | ||
| Zeile 968: | Zeile 964: | ||
--- Finished state OK at 13:27:45.045 - Runtime 00:00:03.329 --- | --- Finished state OK at 13:27:45.045 - Runtime 00:00:03.329 --- | ||
== | ==gpg: Algorithmus pigz anstatt bzip2 verwenden, schlägt fehl== | ||
*'''p'''arallel '''i'''mplementation of '''gz'''ip | *'''p'''arallel '''i'''mplementation of '''gz'''ip | ||
*Nutzt alle CPU-Kerne zum Komprimieren der Archive. | *Nutzt alle CPU-Kerne zum Komprimieren der Archive. | ||
| Zeile 1.006: | Zeile 1.002: | ||
Komprimierung: nicht komprimiert, ZIP, ZLIB, BZIP2 | Komprimierung: nicht komprimiert, ZIP, ZLIB, BZIP2 | ||
= | =Oberflächenanalyse /dev/sdd= | ||
# smartctl -l selftest /dev/sdd | # smartctl -l selftest /dev/sdd | ||
| Zeile 1.026: | Zeile 1.022: | ||
#10 Short offline Completed without error 00% 3498 - | #10 Short offline Completed without error 00% 3498 - | ||
== | ==Werte aller Attribute /dev/sdd== | ||
# smartctl -A /dev/sdd | # smartctl -A /dev/sdd | ||
| Zeile 1.059: | Zeile 1.055: | ||
225 Load_Cycle_Count 0x0032 100 100 000 Old_age Always - 2167 | 225 Load_Cycle_Count 0x0032 100 100 000 Old_age Always - 2167 | ||
= | =Partitionierung - fdisk= | ||
*Bezeichnungen herausfinden | *Bezeichnungen herausfinden | ||
| Zeile 1.125: | Zeile 1.121: | ||
Syncing disks. | Syncing disks. | ||
= | =RAID-Alignment (Ausrichtung)= | ||
*Datenträger, RAID-Verbunde und Dateisysteme fassen Daten jeweils für sich in Blöcke zusammen, bevor sie gespeichert werden. | *Datenträger, RAID-Verbunde und Dateisysteme fassen Daten jeweils für sich in Blöcke zusammen, bevor sie gespeichert werden. | ||
| Zeile 1.136: | Zeile 1.132: | ||
# mdadm -D /dev/md0 | grep "Chunk Size" | # mdadm -D /dev/md0 | grep "Chunk Size" | ||
*Bei einem RAID 5 mit Standardeinstellungen liefert dies | *Bei einem RAID 5 mit Standardeinstellungen liefert dies beispielsweise : | ||
Chunk Size : 512K | Chunk Size : 512K | ||
| Zeile 1.152: | Zeile 1.148: | ||
**'''stripe-width''' - Die Größe eines Datenstreifens, also die Menge an Blöcken, die geschrieben wird, wenn ein voller Chunk auf jedes Laufwerk geschrieben wird. Diese berechnet sich aus '''stride-size * Anzahl der effektiv nutzbaren Partitionen'''. Bei einem RAID 5 über 4 Partitionen ergibt sich hier '''128 * 3 = 384'''. | **'''stripe-width''' - Die Größe eines Datenstreifens, also die Menge an Blöcken, die geschrieben wird, wenn ein voller Chunk auf jedes Laufwerk geschrieben wird. Diese berechnet sich aus '''stride-size * Anzahl der effektiv nutzbaren Partitionen'''. Bei einem RAID 5 über 4 Partitionen ergibt sich hier '''128 * 3 = 384'''. | ||
*Details zur Anzahl der effektiv nutzbaren Partitionen findet man im Artikel [[ | *Details zur Anzahl der effektiv nutzbaren Partitionen findet man im Artikel [[RAID#RAID-Level|RAID]]. | ||
*Sind die Parameter ermittelt, wird das Dateisystem erstellt: | *Sind die Parameter ermittelt, wird das Dateisystem erstellt: | ||
# mkfs.ext4 -b 4096 -E stride=128,stripe-width=384 /dev/md0 | # mkfs.ext4 -b 4096 -E stride=128,stripe-width=384 /dev/md0 | ||
=Netzwerkplan - Ist-Zustand= | |||
[[Datei:NetzwerkplanIst4.jpg|700px|thumb|center]] | |||
=Netzwerkplan - Soll-Konzept= | |||
[[Datei:NetzwerkplanSoll103.jpg|700px|thumb|center]] | |||
=Datenflussdiagramm - rsnapshot/duply= | |||
[[Datei:Dfd101.jpg|700px|thumb|center]] | |||
=Entscheidungsmatrix= | |||
==Kriterien == | |||
===Backup/Server=== | |||
===Backup-Space=== | |||
*Preis pro TB: | |||
**Bezugsgrenze war der Bereich zwischen 2 und 4 TB an Datenspeicher. | |||
*Standort(e): | |||
**Wo genau stehen die Server? | |||
**Wenn Server in mehreren Ländern stehen, kann man den Standort selbst wählen? | |||
*Erweiterbarkeit: | |||
**Wie schnell kann der Datenspeicher nach oben (bzw. unten) skaliert werden? | |||
**Was verändert sich an den Kosten? | |||
*Vertragslaufzeit: | |||
**Wie schnell und flexibel kann der Backspace an sich ändernde Anforderungen angepasst werden? | |||
*Zugriffsprotokolle: | |||
**Anzahl und Art der verwendbaren Protkolle ausreichend? | |||
*Reputation: | |||
**Nach Erfahrungswerten des Kunden/Online-Recherche | |||
== Gewichtung == | |||
=Angebote= | |||
==Backup/Server== | |||
[[Datei:AngebotServerKostenintensivConsumerTech4.jpg|700px|thumb|center]] | |||
=Liste Anbieter Backup-Space = | |||
==Hetzner== | |||
*Link: https://www.hetzner.com/de/storage/storage-box/bx40 | |||
*Preis pro TB: 5,74€/Mon. (2TB) - keine Einrichtungsgebühr | |||
*Standort(e): D, FIN | |||
*Erweiterbarkeit: Up- oder Downgrade jeder Zeit möglich | |||
*Vertragslaufzeit: keine | |||
*Zugriffsprotokolle: FTP, FTPS, SFTP, SCP, HTTPS, WebDAV | |||
==Online-backup-storage== | |||
*Link: https://www.online-backup-storage.de/ | |||
*Preis pro TB: 35,70€ plus Einrichtungsgebühr | |||
*Standort(e): D (Stuttgart) | |||
*Erweiterbarkeit: bis 8 TB | |||
*Vertragslaufzeit: keine Angabe | |||
*Zugriffsprotokolle: SMB Encryption | |||
==Ionos 1== | |||
*Link: https://www.ionos.de/office-loesungen/hidrive-cloud-speicher | |||
*Preis pro TB: 5,00€ (erste 12 Monate), danach 10,00€ | |||
*Standort(e): D | |||
*Erweiterbarkeit: max 2 TB | |||
*Vertragslaufzeit: 1 Monat | |||
*Zugriffsprotokolle: Smartphone App, WebDAV, SMB, Git | |||
==IONOS Cloud Backup Flex== | |||
*Link: https://www.ionos.de/cloud/cloud-backup | |||
*Preis pro TB: 120,00€ (Startguthaben 325,00€, Abrechnung monatlich 0,12Cent/GB, Zahlen nach Verbrauch) | |||
*Standort(e): keine Angabe | |||
*Erweiterbarkeit: keine Angabe | |||
*Vertragslaufzeit: 1 Monat | |||
*Zugriffsprotokolle: keine Angabe - Kryptografie SSL, AES-256 | |||
==Strato HiDrive== | |||
*Link: https://www.strato.de/cloud-speicher/ | |||
*Preis pro TB: 6,00€, keine Einrichtungsgebühr | |||
*Standort(e): D | |||
*Erweiterbarkeit: direkt 3 TB | |||
*Vertragslaufzeit: 12 Monate | |||
*Zugriffsprotokolle: SFTP, FTPS, WebDAV, SMB/CIFS, rsynch, SCP, Git | |||
==LeitzCloud== | |||
*Link: https://leitz-cloud.com/ | |||
*Preis pro TB: 16,00€ | |||
*Standort(e): D | |||
*Erweiterbarkeit: 12,5 TB | |||
*Vertragslaufzeit: keine Angaben | |||
*Zugriffsprotokolle: keien Angaben | |||
=RAID-Eintrag in der /etc/fstab= | |||
# /etc/fstab: static file system information. | |||
# | |||
# Use 'blkid' to print the universally unique identifier for a | |||
# device; this may be used with UUID= as a more robust way to name devices | |||
# that works even if disks are added and removed. See fstab(5). | |||
# | |||
# <file system> <mount point> <type> <options> <dump> <pass> | |||
# / was on /dev/md0 during installation | |||
UUID=c4da2ed2-7ab2-4bd3-94ad-121930037880 / ext4 errors=remount-ro 0 1 | |||
/dev/sr0 /media/cdrom0 udf,iso9660 user,noauto 0 0 | |||
#md1 mit RAID 6 | |||
UUID=7207e28c-25ac-43cc-8ed5-f02d7b816463 /media/daten ext4 errors=remount-ro 0 2 | |||
=Raumplan= | |||
[[Datei:Raumplan5.jpg]] | |||
=vorhandene Infrastruktur= | |||
{| class="wikitable" | |||
|+ | |||
|- | |||
! Backup-Clients !! Funktion !!Betriebssystem !! Ip-Adresse | |||
|- style="text-align:center" | |||
| linncln01.localdomain || Workstation || Debian Testing || 192.168.1.100 | |||
|- style="text-align:center" | |||
| lincln02.localdomain || Workstation || Debian Stable || 192.168.1.200 | |||
|- style="text-align:center" | |||
| debian02.localdomain || Laptop || Debian Testing || 192.168.1.300 | |||
|- style="text-align:center" | |||
| mx10.foxtom.de || Webserver || Debian Stable || 116.202.118.50 | |||
|- style="text-align:center" | |||
| mx20.foxtom.de || Webserver || Debian Stable || 81.169.207.103 | |||
|- style="text-align:center" | |||
| mx50.foxtom.de || Webserver || Debian Stable || 95.216.156.241 | |||
|} | |||
'''NEU: Einträge''' | |||
{| class="wikitable" | |||
|+ | |||
|- style="text-align:center" | |||
! weitere Netzwerk/Hardwaren !! Funktion !!Betriebssystem !! Ip-Adresse | |||
|- style="text-align:center" | |||
| opnsense.localdomain || Router, Firewall, DHCP, DNS || OPNsense || 192.168.1.1 / 91.66.18.81 | |||
|- style="text-align:center" | |||
| TP-Link T2600G-18TS L2 managed || Switch || || 192.168.1.254 | |||
|- style="text-align:center" | |||
| TP-Link EAP330 || WLAN-Access-Point || || 192.168.1.188 | |||
|} | |||
=Glossar= | |||
'''Open-Source-Software''' - Als Open Source (aus englisch open source, wörtlich offene Quelle) wird Software bezeichnet, deren Quelltext öffentlich und von Dritten eingesehen, geändert und genutzt werden kann. Open-Source-Software kann meistens kostenlos genutzt werden. | |||
'''RTO''' - Recover time objetive ist die maximal tolerierbare Länge eines Zeitraums, die ein Computer, IT-System, Netzwerk oder eine Anwendung ausfallen darf. | |||
'''RPO''' - Recovery point objective ist der Zeitraum, der zwischen zwei Backups liegen darf, um den Normalbetrieb nach dem Absturz eines Computers, IT-Systems oder Netzwerks sicherzustellen. | |||
=Protokoll= | =Protokoll= | ||
| Zeile 1.162: | Zeile 1.336: | ||
=Deckblatt (wird bei Seitenanzahl nicht mitgerechnet)= | =Deckblatt (wird bei Seitenanzahl nicht mitgerechnet)= | ||
#Projektbezeichnung: Aufbau und Einrichtung eines Backup | #Projektbezeichnung: Aufbau und Einrichtung eines Backup/Servers in einem LAN für Client-Backups und zusätzlich Einrichtung einer externen Backup-Lösung. | ||
#Namen und Vornamen: Quies, Robert | #Namen und Vornamen: Quies, Robert | ||
#Prüfungsausschuss: ITSE 02 | #Prüfungsausschuss: ITSE 02 | ||
#Ausbildungsberuf: IT-Systemelektroniker | #Ausbildungsberuf: IT-Systemelektroniker | ||
#Ausbildungsstätte bzw. Praktikumsbetrieb: itw gGmbH, Groninger Straße 25, 13347 Berlin bzw. Dirk Wagner Berlin, Carstennstraße 6, 12205 Berlin | #Ausbildungsstätte bzw. Praktikumsbetrieb: itw gGmbH, Groninger Straße 25, 13347 Berlin bzw. Dirk Wagner Berlin, Carstennstraße 6, 12205 Berlin | ||
[[Kategorie:Backup/Server]] | |||
Aktuelle Version vom 28. April 2025, 09:30 Uhr
- Angebot interner Backup/Server
- Angebot externer Backup-Space
- Kundenauftrag
- Raumplan
- Netzwerkplan
- Skizzen
- Schaltplan?
- Config-Datei rsnapshot
- Config-Datei duply
- Ablauf GnuPG: Schlüsselerstellung
- Fotos
- Messprotokolle
rsnapshot.conf
################################################# # rsnapshot.conf - rsnapshot configuration file # ################################################# # # # PLEASE BE AWARE OF THE FOLLOWING RULE: # # # # This file requires tabs between elements # # # ################################################# ####################### # CONFIG FILE VERSION # ####################### config_version 1.2 ########################### # SNAPSHOT ROOT DIRECTORY # ########################### # All snapshots will be stored under this root directory. # snapshot_root /media/daten/rsnapshot/ # If no_create_root is enabled, rsnapshot will not automatically create the # snapshot_root directory. This is particularly useful if you are backing # up to removable media, such as a FireWire or USB drive. # #no_create_root 1 ################################# # EXTERNAL PROGRAM DEPENDENCIES # ################################# # LINUX USERS: Be sure to uncomment "cmd_cp". This gives you extra features. # EVERYONE ELSE: Leave "cmd_cp" commented out for compatibility. # # See the README file or the man page for more details. # cmd_cp /bin/cp # uncomment this to use the rm program instead of the built-in perl routine. # cmd_rm /bin/rm # rsync must be enabled for anything to work. This is the only command that # must be enabled. # cmd_rsync /usr/bin/rsync cmd_ssh /usr/bin/ssh ssh_args -p2227 # Uncomment this to enable remote ssh backups over rsync. # #cmd_ssh /usr/bin/ssh # Comment this out to disable syslog support. # cmd_logger /usr/bin/logger # Uncomment this to specify the path to "du" for disk usage checks. # If you have an older version of "du", you may also want to check the # "du_args" parameter below. # #cmd_du /usr/bin/du # Uncomment this to specify the path to rsnapshot-diff. # #cmd_rsnapshot_diff /usr/bin/rsnapshot-diff # Specify the path to a script (and any optional arguments) to run right # before rsnapshot syncs files # #cmd_preexec /path/to/preexec/script # Specify the path to a script (and any optional arguments) to run right # after rsnapshot syncs files # #cmd_postexec /path/to/postexec/script # Paths to lvcreate, lvremove, mount and umount commands, for use with # Linux LVMs. # #linux_lvm_cmd_lvcreate /sbin/lvcreate #linux_lvm_cmd_lvremove /sbin/lvremove #linux_lvm_cmd_mount /bin/mount #linux_lvm_cmd_umount /bin/umount ######################################### # BACKUP LEVELS / INTERVALS # # Must be unique and in ascending order # # e.g. alpha, beta, gamma, und weitere # ######################################### retain daily 7 retain weekly 4 retain monthly 3 retain quartarly 4 retain annual 2 ############################################ # GLOBAL OPTIONS # # All are optional, with sensible defaults # ############################################ # Verbose level, 1 through 5. # 1 Quiet Print fatal errors only # 2 Default Print errors and warnings only # 3 Verbose Show equivalent shell commands being executed # 4 Extra Verbose Show extra verbose information # 5 Debug mode Everything # verbose 5 # Same as "verbose" above, but controls the amount of data sent to the # logfile, if one is being used. The default is 3. # If you want the rsync output, you have to set it to 4 # loglevel 4 # If you enable this, data will be written to the file you specify. The # amount of data written is controlled by the "loglevel" parameter. # logfile /var/log/rsnapshot.log # If enabled, rsnapshot will write a lockfile to prevent two instances # from running simultaneously (and messing up the snapshot_root). # If you enable this, make sure the lockfile directory is not world # writable. Otherwise anyone can prevent the program from running. # lockfile /var/run/rsnapshot.pid # By default, rsnapshot check lockfile, check if PID is running # and if not, consider lockfile as stale, then start # Enabling this stop rsnapshot if PID in lockfile is not running # #stop_on_stale_lockfile 0 # Default rsync args. All rsync commands have at least these options set. # #rsync_short_args -a #rsync_long_args --delete --numeric-ids --relative --delete- excluded # ssh has no args passed by default, but you can specify some here. # #ssh_args -p 22 # Default arguments for the "du" program (for disk space reporting). # The GNU version of "du" is preferred. See the man page for more details. # If your version of "du" doesn't support the -h flag, try -k flag instead. # #du_args -csh # If this is enabled, rsync won't span filesystem partitions within a # backup point. This essentially passes the -x option to rsync. # The default is 0 (off). # #one_fs 0 # The include and exclude parameters, if enabled, simply get passed directly # to rsync. If you have multiple include/exclude patterns, put each one on a # separate line. Please look up the --include and --exclude options in the # rsync man page for more details on how to specify file name patterns. # #include ??? #include ??? #exclude ??? #exclude ??? # The include_file and exclude_file parameters, if enabled, simply get # passed directly to rsync. Please look up the --include-from and # --exclude-from options in the rsync man page for more details. # #include_file /path/to/include/file #exclude_file /path/to/exclude/file # If your version of rsync supports --link-dest, consider enabling this. # This is the best way to support special files (FIFOs, etc) cross-platform. # The default is 0 (off). # #link_dest 0 # When sync_first is enabled, it changes the default behaviour of rsnapshot. # Normally, when rsnapshot is called with its lowest interval # (i.e.: "rsnapshot alpha"), it will sync files AND rotate the lowest # intervals. With sync_first enabled, "rsnapshot sync" handles the file sync, # and all interval calls simply rotate files. See the man page for more # details. The default is 0 (off). # #sync_first 0 # If enabled, rsnapshot will move the oldest directory for each interval # to [interval_name].delete, then it will remove the lockfile and delete # that directory just before it exits. The default is 0 (off). # #use_lazy_deletes 0 # Number of rsync re-tries. If you experience any network problems or # network card issues that tend to cause ssh to fail with errors like # "Corrupted MAC on input", for example, set this to a non-zero value # to have the rsync operation re-tried. # #rsync_numtries 0 # LVM parameters. Used to backup with creating lvm snapshot before backup # and removing it after. This should ensure consistency of data in some special # cases # # LVM snapshot(s) size (lvcreate --size option). # #linux_lvm_snapshotsize 100M # Name to be used when creating the LVM logical volume snapshot(s). # #linux_lvm_snapshotname rsnapshot # Path to the LVM Volume Groups. # #linux_lvm_vgpath /dev # Mount point to use to temporarily mount the snapshot(s). # #linux_lvm_mountpath /path/to/mount/lvm/snapshot/during/backup ############################### ### BACKUP POINTS / SCRIPTS ### ############################### # LOCALHOST backup root@lincln02:/etc/ media/daten/rsnapshot/ backup root@mx10.foxtom.de:/etc/ media/daten/rsnapshot/ backup root@mx20.foxtom.de:/etc/ media/daten/rsnapshot/ backup root@mx50.foxtom.de:/etc/ media/daten/rsnapshot/ #backup /usr/local/ localhost/ #backup /var/log/rsnapshot localhost/ #backup /etc/passwd localhost/ #backup /home/foo/My Documents/ localhost/ #backup /foo/bar/ localhost/ one_fs=1, rsync_short_args=-urltvpog #backup_script /usr/local/bin/backup_pgsql.sh localhost/postgres/ # You must set linux_lvm_* parameters below before using lvm snapshots #backup lvm://vg0/xen-home/ lvm-vg0/xen-home/ # EXAMPLE.COM #backup_exec /bin/date "+ backup of example.com started at %c" #backup root@example.com:/home/ example.com/ +rsync_long_args=-- bwlimit=16,exclude=core #backup root@example.com:/etc/ example.com/ exclude=mtab,exclude=core #backup_exec ssh root@example.com "mysqldump -A > /var/db/dump/mysql.sql" #backup root@example.com:/var/db/dump/ example.com/ #backup_exec /bin/date "+ backup of example.com ended at %c" # CVS.SOURCEFORGE.NET #backup_script /usr/local/bin/backup_rsnapshot_cvsroot.sh rsnapshot.cvs.sourceforge.net/ # RSYNC.SAMBA.ORG #backup rsync://rsync.samba.org/rsyncftp/ rsync.samba.org/rsyncftp/
duply.conf
# gpg encryption settings, simple settings: # GnuPG_KEY='disabled' - disables encryption alltogether # GnuPG_KEY='<key1>[,<key2>]'; GnuPG_PW='pass' - encrypt with keys, # sign if secret key of key1 is available use GnuPG_PW for sign & decrypt # Note: you can specify keys via all methods described in gpg manpage, # section "How to specify a user ID", escape commas (,) via backslash (\) # e.g. 'Mueller, Horst', 'Bernd' -> 'Mueller\, Horst, Bernd' # as they are used to separate the entries # GnuPG_PW='passphrase' - symmetric encryption using passphrase only GnuPG_KEY='B2E20485FF7FC772 ' GnuPG_PW='roottutgut' # gpg encryption settings in detail (extended settings) # the above settings translate to the following more specific settings # GnuPG_KEYS_ENC='<keyid1>[,<keyid2>,...]' - list of pubkeys to encrypt to # GnuPG_KEY_SIGN='<keyid1>|disabled' - a secret key for signing # GnuPG_PW='<passphrase>' - needed for signing, decryption and symmetric # encryption. If you want to deliver different passphrases for e.g. # several keys or symmetric encryption plus key signing you can use # gpg-agent. Simply make sure that GnuPG_AGENT_INFO is set in environment. # also see "A NOTE ON SYMMETRIC ENCRYPTION AND SIGNING" in duplicity manpage # notes on en/decryption # private key and passphrase will only be needed for decryption or signing. # decryption happens on restore and incrementals (compare archdir contents). # for security reasons it makes sense to separate the signing key from the # encryption keys. https://answers.launchpad.net/duplicity/+question/107216 #GnuPG_KEYS_ENC='<pubkey1>,<pubkey2>,...' #GnuPG_KEY_SIGN='<prvkey>' # set if signing key passphrase differs from encryption (key) passphrase # NOTE: available since duplicity 0.6.14, translates to SIGN_PASSPHRASE #GnuPG_PW_SIGN='<signpass>' # uncomment and set a file path or name force duply to use this gpg executable # available in duplicity 0.7.04 and above (currently unreleased 06/2015) #GnuPG='/usr/local/gpg-2.1/bin/gpg' # gpg options passed from duplicity to gpg process (default=) # e.g. "--trust-model pgp|classic|direct|always" # or "--compress-algo=bzip2 --bzip2-compress-level=9" # or "--personal-cipher-preferences AES256,AES192,AES..." # or "--homedir ~/.duply" - keep keyring and gpg settings duply specific # or "--pinentry-mode loopback" - needed for GnuPG 2.1+ _and_ # also enable allow-loopback-pinentry in your .gnupg/gpg-agent.conf GnuPG_OPTS='--compress-algo=bzip2 --bzip2-compress-level=9 --personal- cipher-preferences AES256' # disable preliminary tests with the following setting #GnuPG_TEST='disabled' # backend, credentials & location of the backup target (URL-Format) # generic syntax is # scheme://[user[:password]@]host[:port]/[/]path # eg. # sftp://bob:secret@backupserver.com//home/bob/dupbkp # for details and available backends see duplicity manpage, section URL Format # https://duplicity.nongnu.org/duplicity.1.html#sect7 # BE AWARE: # some backends (cloudfiles, S3 und weitere) need additional env vars to be set to # work properly, read after the TARGET definition for more details. # ATTENTION: # characters other than A-Za-z0-9.-_.~ in the URL have to be # replaced by their url encoded pendants, see # https://en.wikipedia.org/wiki/Url_encoding # if you define the credentials as TARGET_USER, TARGET_PASS below duply # will try to url_encode them for you if the need arises. TARGET='file:///home/user/zielbackup' # optionally the username/password can be defined as extra variables # setting them here _and_ in TARGET results in an error # ATTENTION: # there are backends that do not support the user/pass auth scheme. # prominent examples are S3, Azure, Cloudfiles. when in doubt consult the # duplicity manpage. usually there is a NOTE section explaining if and which # env vars should be set. #TARGET_USER='_backend_username_' #TARGET_PASS='_backend_password_' # eg. for cloud files backend it might look like this (uncomment for use!) #export CLOUDFILES_USERNAME='someuser' #export CLOUDFILES_APIKEY='somekey' #export CLOUDFILES_AUTHURL ='someurl' # the following is an incomplete list (<backend>: comma separated env vars list) # Azure: AZURE_ACCOUNT_NAME, AZURE_ACCOUNT_KEY # Cloudfiles: CLOUDFILES_USERNAME, CLOUDFILES_APIKEY, CLOUDFILES_AUTHURL # Google Cloud Storage: GS_ACCESS_KEY_ID, GS_SECRET_ACCESS_KEY # Pydrive: GOOGLE_DRIVE_ACCOUNT_KEY, GOOGLE_DRIVE_SETTINGS # S3: AWS_ACCESS_KEY_ID, AWS_SECRET_ACCESS_KEY # Swift: SWIFT_USERNAME, SWIFT_PASSWORD, SWIFT_AUTHURL, # SWIFT_TENANTNAME OR SWIFT_PREAUTHURL, SWIFT_PREAUTHTOKEN # base directory to backup SOURCE='/' # a command that runs duplicity e.g. # shape bandwidth use via trickle # "trickle -s -u 640 -d 5120" # 5Mb up, 40Mb down" #DUPL_PRECMD="" # override the used python interpreter, defaults to # - parsed result of duplicity's shebang or 'python2' # e.g. "python2" or "/usr/bin/python2.7" #PYTHON="python" # exclude folders containing exclusion file (since duplicity 0.5.14) # Uncomment the following two lines to enable this setting. #FILENAME='.duplicity-ignore' #DUPL_PARAMS="$DUPL_PARAMS --exclude-if-present '$FILENAME'" # Time frame for old backups to keep, Used for the "purge" command. # see duplicity man page, chapter TIME_FORMATS) MAX_AGE=1M # Number of full backups to keep. Used for the "purgeFull" command. # See duplicity man page, action "remove-all-but-n-full". MAX_FULL_BACKUPS=1 # Number of full backups for which incrementals will be kept for. # Used for the "purgeIncr" command. # See duplicity man page, action "remove-all-inc-of-but-n-full". #MAX_FULLS_WITH_INCRS=1 # activates duplicity --full-if-older-than option (since duplicity v0.4.4.RC3) # forces a full backup if last full backup reaches a specified age, for the # format of MAX_FULLBKP_AGE see duplicity man page, chapter TIME_FORMATS # Uncomment the following two lines to enable this setting. #MAX_FULLBKP_AGE=1M #DUPL_PARAMS="$DUPL_PARAMS --full-if-older-than $MAX_FULLBKP_AGE " # sets duplicity --volsize option (available since v0.4.3.RC7) # set the size of backup chunks to VOLSIZE MB instead of the default 25MB. # VOLSIZE must be number of MB's to set the volume size to. # Uncomment the following two lines to enable this setting. VOLSIZE=100 DUPL_PARAMS="$DUPL_PARAMS --volsize $VOLSIZE " # verbosity of output (error 0, warning 1-2, notice 3-4, info 5-8, debug 9) # default is 4, if not set VERBOSITY=8 # temporary file space. at least the size of the biggest file in backup # for a successful restoration process. (default is '/tmp', if not set) #TEMP_DIR=/tmp # Modifies archive-dir option (since 0.6.0) Defines a folder that holds # unencrypted meta data of the backup, enabling new incrementals without the # need to decrypt backend metadata first. If empty or deleted somehow, the # private key and it's password are needed. # NOTE: This is confidential data. Put it somewhere safe. It can grow quite # big over time so you might want to put it not in the home dir. # default '~/.cache/duplicity/duply_<profile>/' # if set '${ARCH_DIR}/<profile>' #ARCH_DIR=/some/space/safe/.duply-cache # DEPRECATED setting # sets duplicity --time-separator option (since v0.4.4.RC2) to allow users # to change the time separator from ':' to another character that will work # on their system. HINT: For Windows SMB shares, use --time-separator='_'. # NOTE: '-' is not valid as it conflicts with date separator. # ATTENTION: only use this with duplicity < 0.5.10, since then default file # naming is compatible and this option is pending depreciation #DUPL_PARAMS="$DUPL_PARAMS --time-separator _ " # DEPRECATED setting # activates duplicity --short-filenames option, when uploading to a file # system that can't have filenames longer than 30 characters (e.g. Mac OS 8) # or have problems with ':' as part of the filename (e.g. Microsoft Windows) # ATTENTION: only use this with duplicity < 0.5.10, later versions default file # naming is compatible and this option is pending depreciation #DUPL_PARAMS="$DUPL_PARAMS --short-filenames " # more duplicity command line options can be added in the following way # don't forget to leave a separating space char at the end #DUPL_PARAMS="$DUPL_PARAMS --put_your_options_here "
Konfiguration exclude-Datei
# vi /root/.duply/backuptest/exclude
# although called exclude, this file is actually a globbing file list # duplicity accepts some globbing patterns, even including ones here # here is an example, this incl. only 'dir/bar' except it's subfolder 'foo' # - dir/bar/foo # + dir/bar # - ** # for more details see duplicity manpage, section File Selection # https://duplicity.nongnu.org/duplicity.1.html#sect9 + /etc - **
Erstellung gpg-key
# gpg --full-generate-key
gpg (GnuPG) 2.2.12; Copyright (C) 2018 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Bitte wählen Sie, welche Art von Schlüssel Sie möchten:
(1) RSA und RSA (voreingestellt)
(2) DSA und Elgamal
(3) DSA (nur signieren/beglaubigen)
(4) RSA (nur signieren/beglaubigen)
Ihre Auswahl? 1
RSA-Schlüssel können zwischen 1024 und 4096 Bit lang sein.
Welche Schlüssellänge wünschen Sie? (3072) 4096
Die verlangte Schlüssellänge beträgt 4096 Bit
Bitte wählen Sie, wie lange der Schlüssel gültig bleiben soll.
0 = Schlüssel verfällt nie
<n> = Schlüssel verfällt nach n Tagen
<n>w = Schlüssel verfällt nach n Wochen
<n>m = Schlüssel verfällt nach n Monaten
<n>y = Schlüssel verfällt nach n Jahren
Wie lange bleibt der Schlüssel gültig? (0) 1y
Key verfällt am Do 04 Nov 2021 18:26:30 CET
Ist dies richtig? (j/N) j
GnuPG erstellt eine User-ID, um Ihren Schlüssel identifizierbar zu machen.
Ihr Name ("Vorname Nachname"): Robert Quies
Email-Adresse: raqju@web.de
Kommentar: Es grünt so grün, wenn Spaniens Blüten blühn.
Sie benutzen den Zeichensatz `utf-8'
Sie haben diese User-ID gewählt:
"Robert Quies (Es grünt so grün, wenn Spaniens Blüten blühn.) <raqju@web.de>"
Ändern: (N)ame, (K)ommentar, (E)-Mail oder (F)ertig/(A)bbrechen? F
Wir müssen eine ganze Menge Zufallswerte erzeugen. Sie können dies
unterstützen, indem Sie beispielsweise in einem anderen Fenster/Konsole irgendetwas
tippen, die Maus verwenden oder irgendwelche anderen Programme benutzen.
Wir müssen eine ganze Menge Zufallswerte erzeugen. Sie können dies
unterstützen, indem Sie beispielsweise in einem anderen Fenster/Konsole irgendetwas
tippen, die Maus verwenden oder irgendwelche anderen Programme benutzen.
gpg: /root/.gnupg/trustdb.gpg: trust-db erzeugt
gpg: Schlüssel F47E1B7450082D11 ist als ultimativ vertrauenswürdig gekennzeichnet
gpg: Verzeichnis `/root/.gnupg/openpgp-revocs.d' erzeugt
gpg: Widerrufzertifikat wurde als '/root/.gnupg/openpgp-revocs.d /60E3D3C9ED78CE4A40322BBAF47E1B7450082D11.rev' gespeichert.
Öffentlichen und geheimen Schlüssel erzeugt und signiert.
pub rsa4096 2020-11-04 [SC] [verfällt: 2021-11-04]
60E3D3C9ED78CE4A40322BBAF47E1B7450082D11
uid Robert Quies (Es grünt so grün, wenn Spaniens Blüten blühn.) <raqju@web.de>
sub rsa4096 2020-11-04 [E] [verfällt: 2021-11-04]
Passphrase kann nicht abgefragt werden
Befehl
# duply /root/.duply/Name_Backup_Profil full
Meldung
[GNUPG:] PINENTRY_LAUNCHED 23758 curses 1.1.0 - linux - gpg: Beglaubigung fehlgeschlagen: Unpassender IOCTL (I/O-Control) für das Gerät [GNUPG:] BEGIN_ENCRYPTION 2 9 [GNUPG:] FAILURE sign-encrypt 83918950 gpg: /usr/bin/duply: sign+encrypt failed: Unpassender IOCTL (I/O-Control) für das Gerät
Lösung
echo use-agent >> ~/.gnupg/gpg.conf echo "pinentry-mode loopback" >> ~/.gnupg/gpg.conf echo allow-loopback-pinentry >> ~/.gnupg/gpg-agent.conf
Hintergrund
- Es kommt zu dieser Fehlermeldung, weil gpg die Passphrase nicht automatisch abfragen konnte.
- Die erledigt der gpg-agent, der wiederum pinentry-curses zur sicheren Übertragung der Passphrase vewendet.
- In der gpg.conf muss angegeben werden, dass der gpg-agent verwendet werden soll (use-agent).
- Und in welchem Modus dieser verwendet werden soll (pinentry-mode loopback).
- In der gpg-agent.conf muss dem gpg-agent erlaubt werden den loop-back-pinentry durchzuführen (allow-loopback-pinentry).
Privater ssh-key (RSA) nicht valide
Befehl
# duply /root/.duply/Name_Backup_Profil full
Meldung
# duply /root/.duply/ersatzBU/ full Start duply v2.1, time is 2020-11-10 12:17:27. Using profile '/root/.duply/ersatzBU'. Using installed duplicity version 0.7.18.2, python 2.7.16 (/usr/bin/python2), gpg 2.2.12 (Home: /root/.gnupg), awk 'GNU Awk 4.2.1, API: 2.0 (GNU MPFR 4.0.2, GNU MP 6.1.2)', grep 'grep (GNU grep) 3.3', bash '5.0.3(1)-release (x86_64-pc-linux-gnu)'. Autoset found secret key of first GnuPG_KEY entry '1A955E6287B8E312' for signing. Checking TEMP_DIR '/tmp' is a folder and writable (OK) Test - Encrypt to '1A955E6287B8E312' & Sign with '1A955E6287B8E312' (OK) Test - Decrypt (OK) Test - Compare (OK) Cleanup - Delete '/tmp/duply.3187.1605007047_*'(OK) Backup PUB key '1A955E6287B8E312' to profile. (OK) Write file 'gpgkey.1A955E6287B8E312.pub.asc' (OK) Backup SEC key '1A955E6287B8E312' to profile. (OK) Write file 'gpgkey.1A955E6287B8E312.sec.asc' (OK)
INFO
duply exported new keys to your profile.
You should backup your changed profile folder now and store it in a safe place.
--- Start running command FULL at 12:17:30.512 ---
Using archive dir: /root/.cache/duplicity/duply_ersatzBU
Using backup name: duply_ersatzBU
Import of duplicity.backends.acdclibackend Succeeded
Import of duplicity.backends.azurebackend Succeeded
Import of duplicity.backends.b2backend Succeeded
Import of duplicity.backends.botobackend Succeeded
Import of duplicity.backends.cfbackend Succeeded
Import of duplicity.backends.dpbxbackend Failed: No module named dropbox
Import of duplicity.backends.gdocsbackend Succeeded
Import of duplicity.backends.giobackend Succeeded
Import of duplicity.backends.hsibackend Succeeded
Import of duplicity.backends.hubicbackend Succeeded
Import of duplicity.backends.imapbackend Succeeded
Import of duplicity.backends.lftpbackend Succeeded
Import of duplicity.backends.localbackend Succeeded
Import of duplicity.backends.mediafirebackend Succeeded
Import of duplicity.backends.megabackend Succeeded
Import of duplicity.backends.multibackend Succeeded
Import of duplicity.backends.ncftpbackend Succeeded
Import of duplicity.backends.onedrivebackend Succeeded
Import of duplicity.backends.par2backend Succeeded
Import of duplicity.backends.pydrivebackend Succeeded
Import of duplicity.backends.rsyncbackend Succeeded
Import of duplicity.backends.ssh_paramiko_backend Succeeded
Import of duplicity.backends.ssh_pexpect_backend Succeeded
Import of duplicity.backends.swiftbackend Succeeded
Import of duplicity.backends.sxbackend Succeeded
Import of duplicity.backends.tahoebackend Succeeded
Import of duplicity.backends.webdavbackend Succeeded
/usr/lib/python2.7/dist-packages/paramiko/ecdsakey.py:164: CryptographyDeprecationWarning: Support for unsafe construction of public numbers from encoded data will be removed in a future version. Please use EllipticCurvePublicKey.from_encoded_point
self.ecdsa_curve.curve_class(), pointinfo
ssh: Connected (version 2.0, client OpenSSH_7.5)
Using temporary directory /tmp/duplicity-IXHreI-tempdir
Backend error detail: Traceback (innermost last):
File "/usr/bin/duplicity", line 1567, in <module>
with_tempdir(main)
File "/usr/bin/duplicity", line 1553, in with_tempdir
fn()
File "/usr/bin/duplicity", line 1392, in main
action = commandline.ProcessCommandLine(sys.argv[1:])
File "/usr/lib/python2.7/dist-packages/duplicity/commandline.py", line 1135, in ProcessCommandLine
backup, local_pathname = set_backend(args[0], args[1])
File "/usr/lib/python2.7/dist-packages/duplicity/commandline.py", line 1010, in set_backend
globals.backend = backend.get_backend(bend)
File "/usr/lib/python2.7/dist-packages/duplicity/backend.py", line 223, in get_backend
obj = get_backend_object(url_string)
File "/usr/lib/python2.7/dist-packages/duplicity/backend.py", line 209, in get_backend_object
return factory(pu)
File "/usr/lib/python2.7/dist-packages/duplicity/backends/ssh_paramiko_backend.py", line 235, in __init__
self.config['port'], e))
BackendException: ssh connection to u153662-sub1@u153662.your-storagebox.de:23 failed: not a valid RSA private key file
BackendException: ssh connection to u153662-sub1@u153662.your-storagebox.de:23 failed: not a valid RSA private key file 12:17:31.728 Task 'FULL' failed with exit code '23'. --- Finished state FAILED 'code 23' at 12:17:31.728 - Runtime 00:00:01.216 ---
Lösung
Benötigt duplicity den ssh-key im PEM-Format, wenn duplicity sich via ssh anmelden soll. - Verifiziert durch Duplizierung des Fehlers.
# ssh-keygen -p -f /root/.ssh/id_rsa -m pem -P "" -N ""
Änderung des Formats des ssh-Keys von OPENSSH zu PEM (Privacy-Enhanced Mail)
ssh-keygen
| Option | Beschreibung |
|---|---|
| -p | Fordert die Änderung der Passphrase einer privaten Schlüsseldatei zu ändern, anstatt einen neuen privaten Schlüssel zu erstellen. Das Programm fordert Sie auf, die Datei mit dem privaten Schlüssel, die alte Passphrase und zweimal die neue Passphrase einzugeben. |
| -f | Dateiname. Gibt den Dateinamen der Schlüsseldatei an. Hier der Pfad /root/.ssh/id_rsa |
| -m | Geben Sie ein Schlüsselformat für die Konvertierungsoptionen -i (Import) oder -e (Export) an. Die unterstützten Schlüsselformate sind: "RFC4716" (öffentlicher oder privater RFC 4716 / SSH2-Schlüssel), "PKCS8" (öffentlicher PEM PKCS8-Schlüssel) oder "PEM" (öffentlicher PEM-Schlüssel). Das Standardkonvertierungsformat ist "RFC4716". Wenn Sie beim Generieren oder Aktualisieren eines unterstützten privaten Schlüsseltyps das Format "PEM" festlegen, wird der Schlüssel im alten privaten PEM-Schlüsselformat gespeichert. Hier soll der ssh-key in das PEM-Format konvertiert werden also: -m PEM.
in engl.: Specify a key format for the -i (import) or -e (export) conversion options. The supported key formats are: "RFC4716" (RFC 4716/SSH2 public or private key), "PKCS8" (PEM PKCS8 public key) or "PEM" (PEM public key). The default conversion format is "RFC4716". Setting a format of "PEM" when generating or updating a supported private key type will cause the key to be stored in the legacy PEM private key format. |
| -P | passphrase
Stellt die (alte) Passphrase bereit. |
| -N | new_passphrase
Stellt die neue Passphrase bereit. |
| "Passphrase" | Da hier weder im alten noch im neuen Format für den ssh-key eine Passphrase verwendet wurde bzw. werden soll, wird zwischen den beiden " nichts eingetragen: "" |
Danach klappt es:
# duply /root/.duply/ersatzBU/ full Start duply v2.1, time is 2020-11-10 12:39:16. Using profile '/root/.duply/ersatzBU'. Using installed duplicity version 0.7.18.2, python 2.7.16 (/usr/bin/python2), gpg 2.2.12 (Home: /root/.gnupg), awk 'GNU Awk 4.2.1, API: 2.0 (GNU MPFR 4.0.2, GNU MP 6.1.2)', grep 'grep (GNU grep) 3.3', bash '5.0.3(1)-release (x86_64-pc-linux-gnu)'. Autoset found secret key of first GnuPG_KEY entry '1A955E6287B8E312' for signing. Checking TEMP_DIR '/tmp' is a folder and writable (OK) Test - Encrypt to '1A955E6287B8E312' & Sign with '1A955E6287B8E312' (OK) Test - Decrypt (OK) Test - Compare (OK) Cleanup - Delete '/tmp/duply.3711.1605008357_*'(OK) --- Start running command FULL at 12:39:18.553 --- Using archive dir: /root/.cache/duplicity/duply_ersatzBU Using backup name: duply_ersatzBU Import of duplicity.backends.acdclibackend Succeeded Import of duplicity.backends.azurebackend Succeeded Import of duplicity.backends.b2backend Succeeded Import of duplicity.backends.botobackend Succeeded Import of duplicity.backends.cfbackend Succeeded Import of duplicity.backends.dpbxbackend Failed: No module named dropbox Import of duplicity.backends.gdocsbackend Succeeded Import of duplicity.backends.giobackend Succeeded Import of duplicity.backends.hsibackend Succeeded Import of duplicity.backends.hubicbackend Succeeded Import of duplicity.backends.imapbackend Succeeded Import of duplicity.backends.lftpbackend Succeeded Import of duplicity.backends.localbackend Succeeded Import of duplicity.backends.mediafirebackend Succeeded Import of duplicity.backends.megabackend Succeeded Import of duplicity.backends.multibackend Succeeded Import of duplicity.backends.ncftpbackend Succeeded Import of duplicity.backends.onedrivebackend Succeeded Import of duplicity.backends.par2backend Succeeded Import of duplicity.backends.pydrivebackend Succeeded Import of duplicity.backends.rsyncbackend Succeeded Import of duplicity.backends.ssh_paramiko_backend Succeeded Import of duplicity.backends.ssh_pexpect_backend Succeeded Import of duplicity.backends.swiftbackend Succeeded Import of duplicity.backends.sxbackend Succeeded Import of duplicity.backends.tahoebackend Succeeded Import of duplicity.backends.webdavbackend Succeeded /usr/lib/python2.7/dist-packages/paramiko/ecdsakey.py:164: CryptographyDeprecationWarning: Support for unsafe construction of public numbers from encoded data will be removed in a future version. Please use EllipticCurvePublicKey.from_encoded_point self.ecdsa_curve.curve_class(), pointinfo ssh: Connected (version 2.0, client OpenSSH_7.5) ssh: Authentication (publickey) successful! ssh: [chan 0] Opened sftp connection (server version 3) Reading globbing filelist /root/.duply/ersatzBU/exclude Main action: full ================================================================================ duplicity 0.7.18.2 (October 17, 2018) Args: /usr/bin/duplicity full --name duply_ersatzBU --encrypt-key 1A955E6287B8E312 --sign-key 1A955E6287B8E312 --verbosity 8 --gpg-options --compress-algo=bzip2 --bzip2-compress-level=9 --volsize 100 --exclude-filelist /root/.duply/ersatzBU/exclude / sftp://u153662-sub1@u153662.your-storagebox.de:23/backup Linux debian1 4.19.0-12-amd64 #1 SMP Debian 4.19.152-1 (2020-10-18) x86_64 /usr/bin/python2 2.7.16 (default, Oct 10 2019, 22:02:15) [GCC 8.3.0] ================================================================================ Using temporary directory /tmp/duplicity-isr25J-tempdir Temp has 606838784 available, backup will use approx 136314880. Local and Remote metadata are synchronized, no sync needed. Last full backup date: none Collection Status ----------------- Connecting with backend: BackendWrapper Archive dir: /root/.cache/duplicity/duply_ersatzBU Found 0 secondary backup chains. No backup chains with active signatures found No orphaned or incomplete backup sets found. Reuse configured PASSPHRASE as SIGN_PASSPHRASE Using temporary directory /root/.cache/duplicity/duply_ersatzBU/duplicity-CWEaS8-tempdir Using temporary directory /root/.cache/duplicity/duply_ersatzBU/duplicity-6dFeup-tempdir AsyncScheduler: instantiating at concurrency 0 A . A var A var/cache A var/cache/rsnapshot AsyncScheduler: running task synchronously (asynchronicity disabled) Writing duplicity-full.20201110T113919Z.vol1.difftar.gpg Deleting /tmp/duplicity-isr25J-tempdir/mktemp-iyc8sL-2 AsyncScheduler: task completed successfully Processed volume 1 Writing duplicity-full-signatures.20201110T113919Z.sigtar.gpg Deleting /root/.cache/duplicity/duply_ersatzBU/duplicity-full-signatures.20201110T113919Z.sigtar.gpg Writing duplicity-full.20201110T113919Z.manifest.gpg Deleting /root/.cache/duplicity/duply_ersatzBU/duplicity-full.20201110T113919Z.manifest.gpg --------------[ Backup Statistics ]-------------- StartTime 1605008359.92 (Tue Nov 10 12:39:19 2020) EndTime 1605008359.97 (Tue Nov 10 12:39:19 2020) ElapsedTime 0.04 (0.04 seconds) SourceFiles 4 SourceFileSize 16384 (16.0 KB) NewFiles 4 NewFileSize 16384 (16.0 KB) DeletedFiles 0 ChangedFiles 0 ChangedFileSize 0 (0 bytes) ChangedDeltaSize 0 (0 bytes) DeltaEntries 4 RawDeltaSize 0 (0 bytes) TotalDestinationSizeChange 1582 (1.54 KB) Errors 0 ------------------------------------------------- --- Finished state OK at 12:39:21.932 - Runtime 00:00:03.379 ---
Von synchronen auf asynchronen Modus umstellen
- Arbeitet Backupvorgang effizienter ab.
AsyncScheduler: running task synchronously (asynchronicity disabled)
bei duplicity Option:
--asynchronous-upload
Diese Option in der .duply/conf eintragen unter:
# more duplicity command line options can be added in the following way # don't forget to leave a seperating space char at the end DUPL_PARAMS="$DUPL_PARAMS --asynchronous-upload "
Danach
# duply /root/.duply/ersatzBU/ full Start duply v2.1, time is 2020-11-10 13:27:40. Using profile '/root/.duply/ersatzBU'. Using installed duplicity version 0.7.18.2, python 2.7.16 (/usr/bin/python2), gpg 2.2.12 (Home: /root/.gnupg), awk 'GNU Awk 4.2.1, API: 2.0 (GNU MPFR 4.0.2, GNU MP 6.1.2)', grep 'grep (GNU grep) 3.3', bash '5.0.3(1)-release (x86_64-pc-linux-gnu)'. Autoset found secret key of first GnuPG_KEY entry '1A955E6287B8E312' for signing. Checking TEMP_DIR '/tmp' is a folder and writable (OK) Test - Encrypt to '1A955E6287B8E312' & Sign with '1A955E6287B8E312' (OK) Test - Decrypt (OK) Test - Compare (OK) Cleanup - Delete '/tmp/duply.4565.1605011260_*'(OK) --- Start running command FULL at 13:27:41.716 --- Using archive dir: /root/.cache/duplicity/duply_ersatzBU Using backup name: duply_ersatzBU Import of duplicity.backends.acdclibackend Succeeded Import of duplicity.backends.azurebackend Succeeded Import of duplicity.backends.b2backend Succeeded Import of duplicity.backends.botobackend Succeeded Import of duplicity.backends.cfbackend Succeeded Import of duplicity.backends.dpbxbackend Failed: No module named dropbox Import of duplicity.backends.gdocsbackend Succeeded Import of duplicity.backends.giobackend Succeeded Import of duplicity.backends.hsibackend Succeeded Import of duplicity.backends.hubicbackend Succeeded Import of duplicity.backends.imapbackend Succeeded Import of duplicity.backends.lftpbackend Succeeded Import of duplicity.backends.localbackend Succeeded Import of duplicity.backends.mediafirebackend Succeeded Import of duplicity.backends.megabackend Succeeded Import of duplicity.backends.multibackend Succeeded Import of duplicity.backends.ncftpbackend Succeeded Import of duplicity.backends.onedrivebackend Succeeded Import of duplicity.backends.par2backend Succeeded Import of duplicity.backends.pydrivebackend Succeeded Import of duplicity.backends.rsyncbackend Succeeded Import of duplicity.backends.ssh_paramiko_backend Succeeded Import of duplicity.backends.ssh_pexpect_backend Succeeded Import of duplicity.backends.swiftbackend Succeeded Import of duplicity.backends.sxbackend Succeeded Import of duplicity.backends.tahoebackend Succeeded Import of duplicity.backends.webdavbackend Succeeded /usr/lib/python2.7/dist-packages/paramiko/ecdsakey.py:164: CryptographyDeprecationWarning: Support for unsafe construction of public numbers from encoded data will be removed in a future version. Please use EllipticCurvePublicKey.from_encoded_point self.ecdsa_curve.curve_class(), pointinfo ssh: Connected (version 2.0, client OpenSSH_7.5) ssh: Authentication (publickey) successful! ssh: [chan 0] Opened sftp connection (server version 3) Reading globbing filelist /root/.duply/ersatzBU/exclude Main action: full ================================================================================ duplicity 0.7.18.2 (October 17, 2018) Args: /usr/bin/duplicity full --name duply_ersatzBU --encrypt-key 1A955E6287B8E312 --sign-key 1A955E6287B8E312 --verbosity 8 --gpg-options --compress-algo=bzip2 --bzip2-compress-level=9 --volsize 100 --asynchronous-upload --exclude-filelist /root/.duply/ersatzBU/exclude / sftp://u153662-sub1@u153662.your-storagebox.de:23/backup Linux debian1 4.19.0-12-amd64 #1 SMP Debian 4.19.152-1 (2020-10-18) x86_64 /usr/bin/python2 2.7.16 (default, Oct 10 2019, 22:02:15) [GCC 8.3.0] ================================================================================ Using temporary directory /tmp/duplicity-lFN02I-tempdir Temp has 606838784 available, backup will use approx 241172480. Local and Remote metadata are synchronized, no sync needed. Last full backup date: Tue Nov 10 12:39:19 2020 Collection Status ----------------- Connecting with backend: BackendWrapper Archive dir: /root/.cache/duplicity/duply_ersatzBU Found 0 secondary backup chains. Found primary backup chain with matching signature chain: ------------------------- Chain start time: Tue Nov 10 12:39:19 2020 Chain end time: Tue Nov 10 12:39:19 2020 Number of contained backup sets: 1 Total number of contained volumes: 1 Type of backup set: Time: Num volumes: Full Tue Nov 10 12:39:19 2020 1 ------------------------- No orphaned or incomplete backup sets found. Reuse configured PASSPHRASE as SIGN_PASSPHRASE Using temporary directory /root/.cache/duplicity/duply_ersatzBU/duplicity-h7ERXb-tempdir Using temporary directory /root/.cache/duplicity/duply_ersatzBU/duplicity-sHK2KZ-tempdir AsyncScheduler: instantiating at concurrency 1 A . A var A var/cache A var/cache/rsnapshot AsyncScheduler: scheduling task for asynchronous execution Processed volume 1 Writing duplicity-full.20201110T122742Z.vol1.difftar.gpg Deleting /tmp/duplicity-lFN02I-tempdir/mktemp-6T80j7-2 AsyncScheduler: task execution done (success: True) Writing duplicity-full-signatures.20201110T122742Z.sigtar.gpg Deleting /root/.cache/duplicity/duply_ersatzBU/duplicity-full-signatures.20201110T122742Z.sigtar.gpg Writing duplicity-full.20201110T122742Z.manifest.gpg Deleting /root/.cache/duplicity/duply_ersatzBU/duplicity-full.20201110T122742Z.manifest.gpg --------------[ Backup Statistics ]-------------- StartTime 1605011263.12 (Tue Nov 10 13:27:43 2020) EndTime 1605011263.14 (Tue Nov 10 13:27:43 2020) ElapsedTime 0.02 (0.02 seconds) SourceFiles 4 SourceFileSize 16384 (16.0 KB) NewFiles 4 NewFileSize 16384 (16.0 KB) DeletedFiles 0 ChangedFiles 0 ChangedFileSize 0 (0 bytes) ChangedDeltaSize 0 (0 bytes) DeltaEntries 4 RawDeltaSize 0 (0 bytes) TotalDestinationSizeChange 1593 (1.56 KB) Errors 0 ------------------------------------------------- --- Finished state OK at 13:27:45.045 - Runtime 00:00:03.329 ---
gpg: Algorithmus pigz anstatt bzip2 verwenden, schlägt fehl
- parallel implementation of gzip
- Nutzt alle CPU-Kerne zum Komprimieren der Archive.
- Resultat pigz wird weder von gpg noch gpg2 unterstützt.
# gpg --version gpg (GnuPG) 2.2.12 libgcrypt 1.8.4 Copyright (C) 2018 Free Software Foundation, Inc. License GPLv3+: GNU GPL version 3 or later <https://gnu.org/licenses/gpl.html> This is free software: you are free to change and redistribute it. There is NO WARRANTY, to the extent permitted by law. Home: /root/.gnupg Unterstützte Verfahren: Öff. Schlüssel: RSA, ELG, DSA, ECDH, ECDSA, EDDSA Verschlü.: IDEA, 3DES, CAST5, BLOWFISH, AES, AES192, AES256, TWOFISH, CAMELLIA128, CAMELLIA192, CAMELLIA256 Hash: SHA1, RIPEMD160, SHA256, SHA384, SHA512, SHA224 Komprimierung: nicht komprimiert, ZIP, ZLIB, BZIP2
# gpg2 --version gpg (GnuPG) 2.2.12 libgcrypt 1.8.4 Copyright (C) 2018 Free Software Foundation, Inc. License GPLv3+: GNU GPL version 3 or later <https://gnu.org/licenses/gpl.html> This is free software: you are free to change and redistribute it. There is NO WARRANTY, to the extent permitted by law. Home: /root/.gnupg Unterstützte Verfahren: Öff. Schlüssel: RSA, ELG, DSA, ECDH, ECDSA, EDDSA Verschlü.: IDEA, 3DES, CAST5, BLOWFISH, AES, AES192, AES256, TWOFISH, CAMELLIA128, CAMELLIA192, CAMELLIA256 Hash: SHA1, RIPEMD160, SHA256, SHA384, SHA512, SHA224 Komprimierung: nicht komprimiert, ZIP, ZLIB, BZIP2
Oberflächenanalyse /dev/sdd
# smartctl -l selftest /dev/sdd smartctl 6.6 2017-11-05 r4594 [x86_64-linux-4.19.0-12-amd64] (local build) Copyright (C) 2002-17, Bruce Allen, Christian Franke, www.smartmontools.org === START OF READ SMART DATA SECTION === SMART Self-test log structure revision number 1 Num Test_Description Status Remaining LifeTime(hours) LBA_of_first_error # 1 Extended offline Completed without error 00% 14712 - # 2 Short offline Completed without error 00% 14464 - # 3 Extended offline Completed without error 00% 14454 - # 4 Short offline Completed without error 00% 14443 - # 5 Extended offline Aborted by host 40% 14292 - # 6 Extended offline Completed without error 00% 14214 - # 7 Short offline Completed without error 00% 14212 - # 8 Extended offline Completed without error 00% 12438 - # 9 Short offline Completed without error 00% 8832 - #10 Short offline Completed without error 00% 3498 -
Werte aller Attribute /dev/sdd
# smartctl -A /dev/sdd smartctl 6.6 2017-11-05 r4594 [x86_64-linux-4.19.0-12-amd64] (local build) Copyright (C) 2002-17, Bruce Allen, Christian Franke, www.smartmontools.org === START OF READ SMART DATA SECTION === SMART Attributes Data Structure revision number: 16 Vendor Specific SMART Attributes with Thresholds: ID# ATTRIBUTE_NAME FLAG VALUE WORST THRESH TYPE UPDATED WHEN_FAILED RAW_VALUE 1 Raw_Read_Error_Rate 0x002f 100 100 051 Pre-fail Always - 96 2 Throughput_Performance 0x0026 055 055 000 Old_age Always - 8674 3 Spin_Up_Time 0x0023 070 068 025 Pre-fail Always - 9391 4 Start_Stop_Count 0x0032 098 098 000 Old_age Always - 2093 5 Reallocated_Sector_Ct 0x0033 252 252 010 Pre-fail Always - 0 7 Seek_Error_Rate 0x002e 252 252 051 Old_age Always - 0 8 Seek_Time_Performance 0x0024 252 252 015 Old_age Offline - 0 9 Power_On_Hours 0x0032 100 100 000 Old_age Always - 14714 10 Spin_Retry_Count 0x0032 252 252 051 Old_age Always - 0 11 Calibration_Retry_Count 0x0032 252 252 000 Old_age Always - 0 12 Power_Cycle_Count 0x0032 098 098 000 Old_age Always - 2114 191 G-Sense_Error_Rate 0x0022 100 100 000 Old_age Always - 1 192 Power-Off_Retract_Count 0x0022 252 252 000 Old_age Always - 0 194 Temperature_Celsius 0x0002 064 052 000 Old_age Always - 35 (Min/Max 9/48) 195 Hardware_ECC_Recovered 0x003a 100 100 000 Old_age Always - 0 196 Reallocated_Event_Count 0x0032 252 252 000 Old_age Always - 0 197 Current_Pending_Sector 0x0032 252 252 000 Old_age Always - 0 198 Offline_Uncorrectable 0x0030 252 252 000 Old_age Offline - 0 199 UDMA_CRC_Error_Count 0x0036 100 100 000 Old_age Always - 1 200 Multi_Zone_Error_Rate 0x002a 100 100 000 Old_age Always - 12783 223 Load_Retry_Count 0x0032 252 252 000 Old_age Always - 0 225 Load_Cycle_Count 0x0032 100 100 000 Old_age Always - 2167
Partitionierung - fdisk
- Bezeichnungen herausfinden
#fdisk -l
- Datenträger partitionieren
# fdisk /dev/sdc
Welcome to fdisk (util-linux 2.33.1). Changes will remain in memory only, until you decide to write them. Be careful before using the write command. Device does not contain a recognized partition table. Created a new DOS disklabel with disk identifier 0xdfca4904. Command (m for help):
- GPT (GUID-Partition-Table) wird angelegt.
Command (m for help): g
Created a new GPT disklabel (GUID: 748568BC-EC8C-F34A-B822-45C2E267CFFB).
- Partitionstabelle anlegen
Command (m for help): n
Partition number (1-128, default 1): 1
First sector (2048-3907029134, default 2048): 2048
Last sector, +/-sectors or +/-size{K,M,G,T,P} (2048-3907029134, default 3907029134): +1842G
Created a new partition 1 of type 'Linux filesystem' and of size 1,8 TiB.
- Partition als RAID-Partition markieren
Command (m for help): t
Selected partition 1 Partition type (type L to list all types): 29
Changed type of partition 'Linux filesystem' to 'Linux RAID'.
- Änderungen auf Korrektheit überprüfen
Command (m for help): p
Disk /dev/sdc: 1,8 TiB, 2000398934016 bytes, 3907029168 sectors Disk model: WDC WD20EZRX-00D Units: sectors of 1 * 512 = 512 bytes Sector size (logical/physical): 512 bytes / 4096 bytes I/O size (minimum/optimal): 4096 bytes / 4096 bytes Disklabel type: gpt Disk identifier: 748568BC-EC8C-F34A-B822-45C2E267CFFB Device Start End Sectors Size Type /dev/sdc1 2048 3862956031 3862953984 1,8T Linux RAID
- Änderungen schreiben
Command (m for help): w
The partition table has been altered. Calling ioctl() to re-read partition table. Syncing disks.
RAID-Alignment (Ausrichtung)
- Datenträger, RAID-Verbunde und Dateisysteme fassen Daten jeweils für sich in Blöcke zusammen, bevor sie gespeichert werden.
- Diese Blöcke haben im Allgemeinen alle unterschiedliche Größen.
- Um eine optimale Performance zu erzielen, sollten die Größen aufeinander abgestimmt sein.
- Dafür muss zunächst die sog. Chunk Size, also die Datenmenge, die in einem einzelnen Schreibvorgang geschrieben wird, bekannt sein.
Ermittlung der Chunk Size
# mdadm -D /dev/md0 | grep "Chunk Size"
- Bei einem RAID 5 mit Standardeinstellungen liefert dies beispielsweise :
Chunk Size : 512K
- Es werden also 512 KiB Chunks verwendet.
Berechnung des Alignments
- Hieraus können, zusammen mit der Anzahl der Partitionen und des RAID-Levels, die Dateisystem-Parameter berechnet werden.
- Am einfachsten geht das mittels eines Raid-Stride-Calculators.
- Alternativ können die Parameter auch von Hand ermittelt werden.
- block-size - Die Größe der Dateisystemblöcke in Bytes. Heutzutage werden fast ausschließlich 4096 Byte (4 KiB) Blöcke verwendet.
- stride-size - Die Chunk Size umgerechnet in Dateisystemblöcke. Bei 512 KiB Chunk Size mit 4 KiB Blöcken ergibt sich 512 KiB/ 4 KiB = 128.
- stripe-width - Die Größe eines Datenstreifens, also die Menge an Blöcken, die geschrieben wird, wenn ein voller Chunk auf jedes Laufwerk geschrieben wird. Diese berechnet sich aus stride-size * Anzahl der effektiv nutzbaren Partitionen. Bei einem RAID 5 über 4 Partitionen ergibt sich hier 128 * 3 = 384.
- Details zur Anzahl der effektiv nutzbaren Partitionen findet man im Artikel RAID.
- Sind die Parameter ermittelt, wird das Dateisystem erstellt:
# mkfs.ext4 -b 4096 -E stride=128,stripe-width=384 /dev/md0
Netzwerkplan - Ist-Zustand
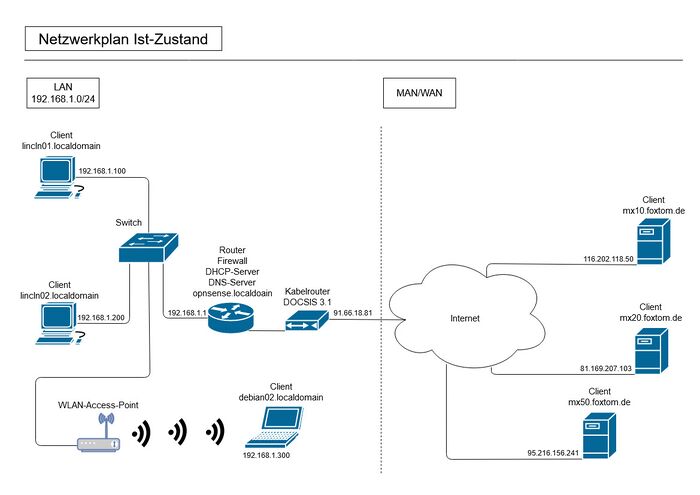
Netzwerkplan - Soll-Konzept
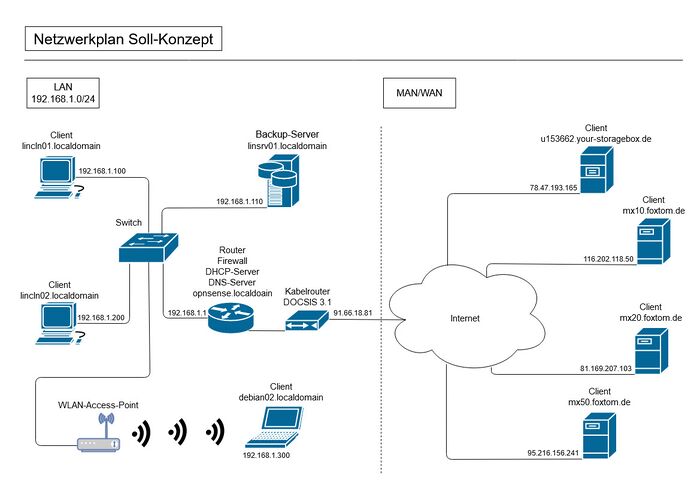
Datenflussdiagramm - rsnapshot/duply
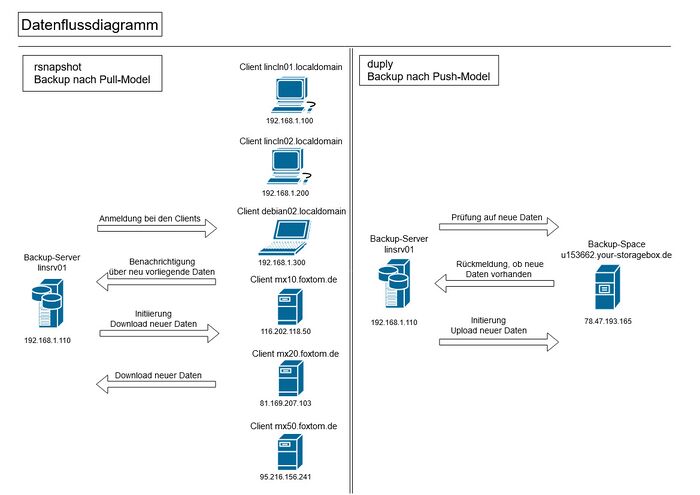
Entscheidungsmatrix
Kriterien
Backup/Server
Backup-Space
- Preis pro TB:
- Bezugsgrenze war der Bereich zwischen 2 und 4 TB an Datenspeicher.
- Standort(e):
- Wo genau stehen die Server?
- Wenn Server in mehreren Ländern stehen, kann man den Standort selbst wählen?
- Erweiterbarkeit:
- Wie schnell kann der Datenspeicher nach oben (bzw. unten) skaliert werden?
- Was verändert sich an den Kosten?
- Vertragslaufzeit:
- Wie schnell und flexibel kann der Backspace an sich ändernde Anforderungen angepasst werden?
- Zugriffsprotokolle:
- Anzahl und Art der verwendbaren Protkolle ausreichend?
- Reputation:
- Nach Erfahrungswerten des Kunden/Online-Recherche
Gewichtung
Angebote
Backup/Server

Liste Anbieter Backup-Space
Hetzner
- Preis pro TB: 5,74€/Mon. (2TB) - keine Einrichtungsgebühr
- Standort(e): D, FIN
- Erweiterbarkeit: Up- oder Downgrade jeder Zeit möglich
- Vertragslaufzeit: keine
- Zugriffsprotokolle: FTP, FTPS, SFTP, SCP, HTTPS, WebDAV
Online-backup-storage
- Preis pro TB: 35,70€ plus Einrichtungsgebühr
- Standort(e): D (Stuttgart)
- Erweiterbarkeit: bis 8 TB
- Vertragslaufzeit: keine Angabe
- Zugriffsprotokolle: SMB Encryption
Ionos 1
- Preis pro TB: 5,00€ (erste 12 Monate), danach 10,00€
- Standort(e): D
- Erweiterbarkeit: max 2 TB
- Vertragslaufzeit: 1 Monat
- Zugriffsprotokolle: Smartphone App, WebDAV, SMB, Git
IONOS Cloud Backup Flex
- Preis pro TB: 120,00€ (Startguthaben 325,00€, Abrechnung monatlich 0,12Cent/GB, Zahlen nach Verbrauch)
- Standort(e): keine Angabe
- Erweiterbarkeit: keine Angabe
- Vertragslaufzeit: 1 Monat
- Zugriffsprotokolle: keine Angabe - Kryptografie SSL, AES-256
Strato HiDrive
- Preis pro TB: 6,00€, keine Einrichtungsgebühr
- Standort(e): D
- Erweiterbarkeit: direkt 3 TB
- Vertragslaufzeit: 12 Monate
- Zugriffsprotokolle: SFTP, FTPS, WebDAV, SMB/CIFS, rsynch, SCP, Git
LeitzCloud
- Link: https://leitz-cloud.com/
- Preis pro TB: 16,00€
- Standort(e): D
- Erweiterbarkeit: 12,5 TB
- Vertragslaufzeit: keine Angaben
- Zugriffsprotokolle: keien Angaben
RAID-Eintrag in der /etc/fstab
# /etc/fstab: static file system information. # # Use 'blkid' to print the universally unique identifier for a # device; this may be used with UUID= as a more robust way to name devices # that works even if disks are added and removed. See fstab(5). # # <file system> <mount point> <type> <options> <dump> <pass> # / was on /dev/md0 during installation UUID=c4da2ed2-7ab2-4bd3-94ad-121930037880 / ext4 errors=remount-ro 0 1 /dev/sr0 /media/cdrom0 udf,iso9660 user,noauto 0 0 #md1 mit RAID 6 UUID=7207e28c-25ac-43cc-8ed5-f02d7b816463 /media/daten ext4 errors=remount-ro 0 2
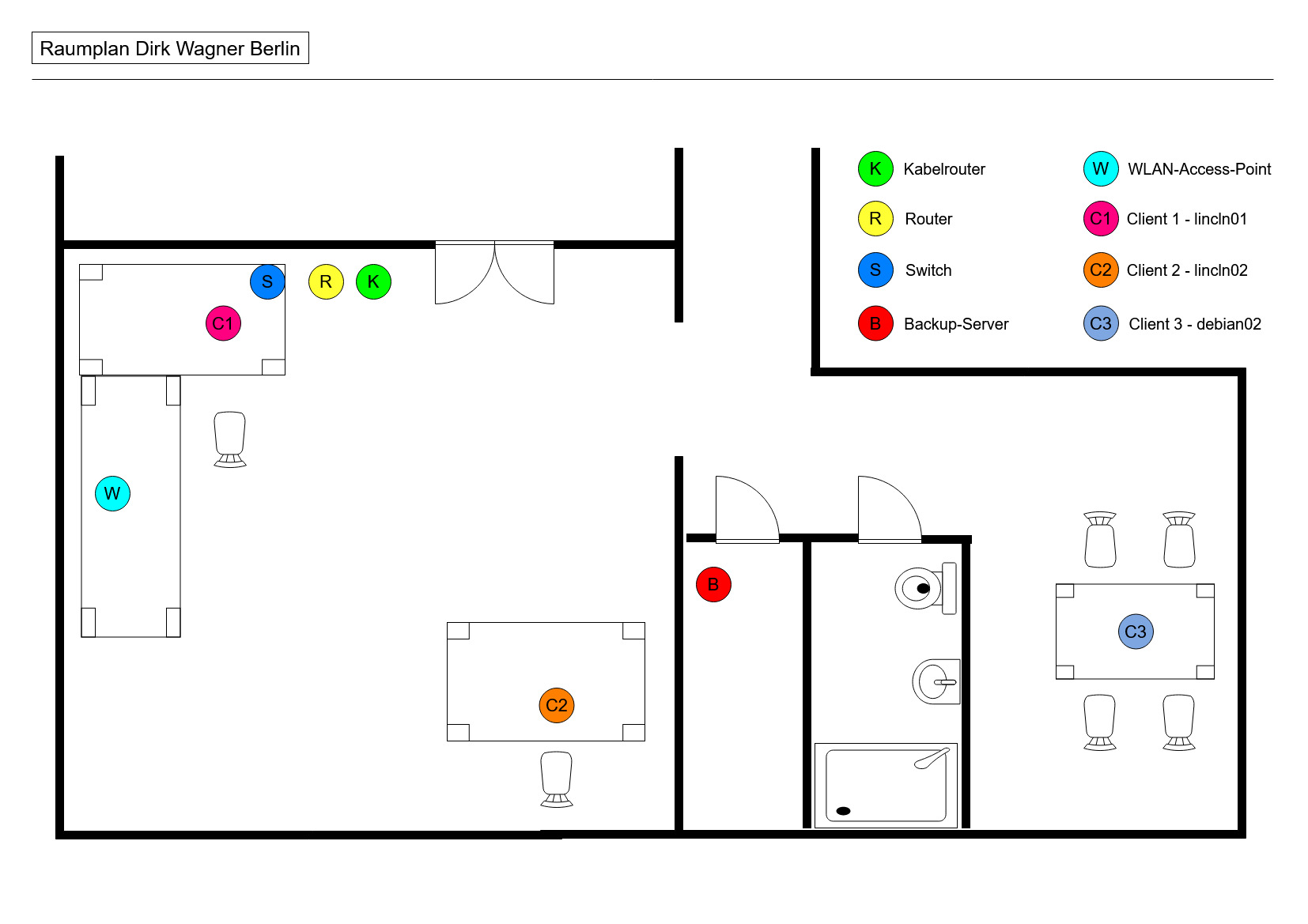
Raumplan
vorhandene Infrastruktur
| Backup-Clients | Funktion | Betriebssystem | Ip-Adresse |
|---|---|---|---|
| linncln01.localdomain | Workstation | Debian Testing | 192.168.1.100 |
| lincln02.localdomain | Workstation | Debian Stable | 192.168.1.200 |
| debian02.localdomain | Laptop | Debian Testing | 192.168.1.300 |
| mx10.foxtom.de | Webserver | Debian Stable | 116.202.118.50 |
| mx20.foxtom.de | Webserver | Debian Stable | 81.169.207.103 |
| mx50.foxtom.de | Webserver | Debian Stable | 95.216.156.241 |
NEU: Einträge
| weitere Netzwerk/Hardwaren | Funktion | Betriebssystem | Ip-Adresse |
|---|---|---|---|
| opnsense.localdomain | Router, Firewall, DHCP, DNS | OPNsense | 192.168.1.1 / 91.66.18.81 |
| TP-Link T2600G-18TS L2 managed | Switch | 192.168.1.254 | |
| TP-Link EAP330 | WLAN-Access-Point | 192.168.1.188 |
Glossar
Open-Source-Software - Als Open Source (aus englisch open source, wörtlich offene Quelle) wird Software bezeichnet, deren Quelltext öffentlich und von Dritten eingesehen, geändert und genutzt werden kann. Open-Source-Software kann meistens kostenlos genutzt werden.
RTO - Recover time objetive ist die maximal tolerierbare Länge eines Zeitraums, die ein Computer, IT-System, Netzwerk oder eine Anwendung ausfallen darf.
RPO - Recovery point objective ist der Zeitraum, der zwischen zwei Backups liegen darf, um den Normalbetrieb nach dem Absturz eines Computers, IT-Systems oder Netzwerks sicherzustellen.
Protokoll
Deckblatt (wird bei Seitenanzahl nicht mitgerechnet)
- Projektbezeichnung: Aufbau und Einrichtung eines Backup/Servers in einem LAN für Client-Backups und zusätzlich Einrichtung einer externen Backup-Lösung.
- Namen und Vornamen: Quies, Robert
- Prüfungsausschuss: ITSE 02
- Ausbildungsberuf: IT-Systemelektroniker
- Ausbildungsstätte bzw. Praktikumsbetrieb: itw gGmbH, Groninger Straße 25, 13347 Berlin bzw. Dirk Wagner Berlin, Carstennstraße 6, 12205 Berlin