Nextcloud/Sicherheitsscanner: Unterschied zwischen den Versionen
| Zeile 10: | Zeile 10: | ||
* This security check is for Nextcloud cloud servers only | * This security check is for Nextcloud cloud servers only | ||
* Nextcloud cannot guarantee exact and/or proper results with other cloud servers than Nextcloud | * Nextcloud cannot guarantee exact and/or proper results with other cloud servers than Nextcloud | ||
=== Notes === | |||
* Our scan is strictly based on '''publicly available information''', that is the list of known vulnerabilities relevant for ownCloud/Nextcloud releases as well as any applied hardenings/settings we can scan without having access to the server. | |||
* Find more hardening tips [https://docs.nextcloud.com/server/latest/admin_manual/installation/harden_server.html in our hardening guide] and keep your system up to date. | |||
* This is no more than a snapshot in time. | |||
* Security is an ongoing process and new insights and updates have to be applied to remain secure. | |||
* No complicated system can ever be fully secure and even an A+ rated system can be vulnerable to unknown issues and determined (state) attackers. | |||
* The rating is automatically generated based on the list of applicable security advisories. | |||
* The actual risk depends on your environment and may differ. | |||
The rating is calculated as follows: | |||
{| class="wikitable sortable" | |||
|- | |||
! Option !! Beschreibung | |||
|- | |||
| F || This server version is end of life and has no security fixes anymore. It is likely trivial to break in and steal all the data or even take over the entire server. | |||
|- | |||
| E || This server is vulnerable to at least one vulnerability rated "high". It is likely quite easy to break in and steal data or even take over the server. | |||
|- | |||
| D || This server is vulnerable to at least one vulnerability rated "medium". With bit of effort, like creating a specially crafted URL and luring a user there, an attacker can likely steal data or even take over the server. | |||
|- | |||
| C || This server is vulnerable to at least one vulnerability rated "low". This might or might not provide a way in for an attacker and will likely need some additional vulnerabilities to be exploited. | |||
|- | |||
| A || This server has no known vulnerabilities but there are additional hardening capabilities available in newer versions making it harder for an attacker to exploit unknown vulnerabilities to break in. | |||
|- | |||
| A+ || This server is up to date, well configured and has industry leading hardening features applied, making it harder for an attacker to exploit unknown vulnerabilities to break in. [https://nextcloud.com/blog/nextcloud-11-delivers-verified-security-improvements Learn more about these preventive hardening features.] | |||
|} | |||
== Anwendungen == | == Anwendungen == | ||
Version vom 22. November 2022, 10:31 Uhr
Der Nextcloud Sicherheitsscanner prüft die Sicherheit eines Nextcloud-Servers
Beschreibung
- Sicherheitsanalyse eines Nextcloud-Servers
- Verbesserungsvorschläge
- Updates
- Konfiguration
Disclaimer
- This security check is for Nextcloud cloud servers only
- Nextcloud cannot guarantee exact and/or proper results with other cloud servers than Nextcloud
Notes
- Our scan is strictly based on publicly available information, that is the list of known vulnerabilities relevant for ownCloud/Nextcloud releases as well as any applied hardenings/settings we can scan without having access to the server.
- Find more hardening tips in our hardening guide and keep your system up to date.
- This is no more than a snapshot in time.
- Security is an ongoing process and new insights and updates have to be applied to remain secure.
- No complicated system can ever be fully secure and even an A+ rated system can be vulnerable to unknown issues and determined (state) attackers.
- The rating is automatically generated based on the list of applicable security advisories.
- The actual risk depends on your environment and may differ.
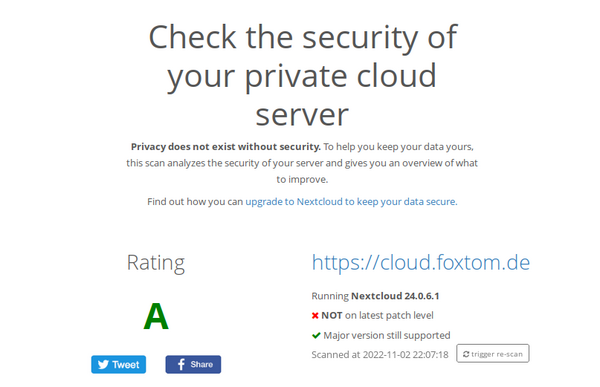
The rating is calculated as follows:
| Option | Beschreibung |
|---|---|
| F | This server version is end of life and has no security fixes anymore. It is likely trivial to break in and steal all the data or even take over the entire server. |
| E | This server is vulnerable to at least one vulnerability rated "high". It is likely quite easy to break in and steal data or even take over the server. |
| D | This server is vulnerable to at least one vulnerability rated "medium". With bit of effort, like creating a specially crafted URL and luring a user there, an attacker can likely steal data or even take over the server. |
| C | This server is vulnerable to at least one vulnerability rated "low". This might or might not provide a way in for an attacker and will likely need some additional vulnerabilities to be exploited. |
| A | This server has no known vulnerabilities but there are additional hardening capabilities available in newer versions making it harder for an attacker to exploit unknown vulnerabilities to break in. |
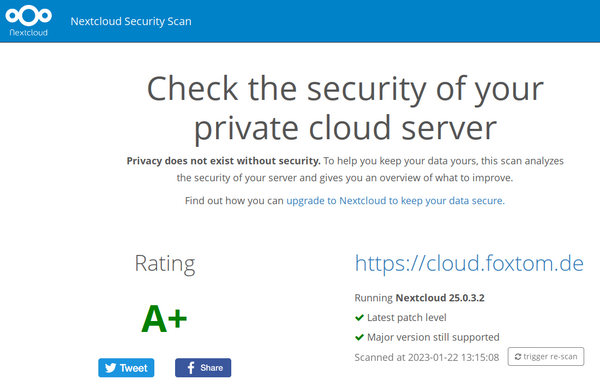
| A+ | This server is up to date, well configured and has industry leading hardening features applied, making it harder for an attacker to exploit unknown vulnerabilities to break in. Learn more about these preventive hardening features. |
Anwendungen
Re-Scan
- Ergebnisse können durch "trigger re-scan" aktualisiert werden
Hardenings
A security hardening is a feature which protects software from attacks even if it is affected by a certain vulnerability.
- For an overview of security hardening capabilities we've developed, see our website.
Below is a list of hardening features your server has enabled.
Bruteforce protection
Bruteforce protection slows down the speed at which passwords can be tried, protecting against an attacker trying to guess a password.
- There have been bruteforce attacks against ownCloud/Nextcloud systems.
CSPv3
CSP is a HTTP feature that allows the server to set specific restrictions on a resource when opened in a browser.
- Such as only allowing to load images or JavaScript from specific targets.
- Using CSP makes it much harder for attackers to exploit a Cross-Site Scripting vulnerability.
- This is the fact because resources inserted by an attacker are not in the whitelist of the policy and thus the browser can notice an injection and refuse execution.
CSP v3.0 makes it possible to have an even stricter policy.
- Instead of restricting the JavaScript inclusion policy to 'self' you can use nonces, which prevents also "mime confusion attacks".
- See the CSP evaluator to evaluate the CSP policy of an application.
Same-Site-Cookies
Same-Site cookies are a security measure supported by modern browsers that prevent CSRF vulnerabilities and protect your privacy further.
Browsers that support same-site cookies can be instructed in a way to only send a cookie if the request is originating from the original domain.
- This makes exploiting CSRF vulnerabilities from other domains a non-issue.
- Also timing attacks, such as enumerating whether a specific file or folder exists, are not feasible anymore.
- Nextcloud enforces the same-site cookies to be present on every request by enforcing this within the request middle ware.
Password confirmation
If an administrator or regular user is trying to change a potential sensitive setting (such as changing the permissions of an user) they will have to provide their password a second time to verify the action.
- Password verification is only required once every 30 minutes.
- After 30 minutes have been passed after the last verification the user will have to re-verify their identity if they make a security-sensitive change.
Checks passwords against HaveIBeenPwned database
In Nextcloud 13.0.1 we added a check against the HaveIBeenPwned database of security researcher Troy Hunt.
- This ensures users can't pick passwords which are known insecure.
__Host-Prefix
The __Host prefix mitigates cookie injection vulnerabilities within potential third-party software sharing the same second level domain.
- It is an additional hardening on top of 'normal' same-site cookies.
App passwords can be restricted
When two-factor authentication is used, Nextcloud users can use tokens instead of their password.
- They are used for apps which don't support 2FA yet.
- By putting specific limitations on things like file system access for apps that don't need it, users can connect their potentially less trusted third-party clients (for example a mobile phone calendar app) without exposing access to all their data.
Setup
Besides features of the private cloud software itself, one can configure their Apache or NGINX server more or less securely.
- Please note that many security settings available cannot be checked from the outside! We strongly recommend you read our Security Hardening Guide and follow the instructions there.
- Here are the results of a number of checks against your server.
Headers
X-Frame-Options
The X-Frame-Options response header indicates whether a page can be iframed by other pages.
- An incorrect setting may allow so called "Clickjacking" attacks.
X-Content-Type-Options
The X-Content-Type-Options response header forbids browsers to guess the Content-Type of a file, this prevents so called "MIME confusion attacks".
X-XSS-Protection
The X-XSS-Protection response header prevents browsers from loading a page when they detect a reflected Cross-Site Scripting attack.
- While not really required anymore for up-to-date browsers this is a decent security hardening for older browsers.
X-Download-Options
The X-Download-Options response header instructs Internet Explorer not to open the file directly but to offer it for download first.
- This mitigates some potential Social Engineering attacks.
X-Permitted-Cross-Domain-Policies
The X-Permitted-Cross-Domain-Policies response header instructs Adobe software on how to handle cross-domain policies.
- This provides a decent security hardening as it restricts Adobe Flash Player's access to data.
Recommendation
We strongly recommend to keep a private cloud server constantly updated.
- Servers not running the latest security update in a supported release series are often vulnerable.
- You can find new versions here for Nextcloud and here for ownCloud. Nextcloud strives to make upgrading a safe, easy and painless procedure.
- As a result of these efforts, for users running PHP 7.x and a current version of Nextcloud, there is no need to re-enable apps upon upgrade and users get notified of new versions of apps as well.
- More improvements are coming! You can learn why and how to upgrade to the latest version of Nextcloud in our earlier blog.
We further recommend to read our Security Hardening Guide and follow the instructions there.
Let us help you keep your data secure
Our customers get proactive help with upgrading and keeping their systems secure.
- We also warn them in advance when security problems are found. Learn about Nextcloud's security efforts.
If you are interested in our services, we have a special time limited offer for prospective customers who can show us a copy of the email warning them of an unsafe instance.
Dokumentation
Siehe auch
Links
Projekt-Homepage
Weblinks
- Find out how you can upgrade to Nextcloud to keep your data secure.
- Learn more about our security efforts.
Einzelnachweise
Testfragen
Testfrage 1
Testfrage 2
Testfrage 3
Testfrage 4
Testfrage 5