ISO/27005: Unterschied zwischen den Versionen
Erscheinungsbild
| Zeile 30: | Zeile 30: | ||
<br clear=all> | <br clear=all> | ||
== Inhalte == | |||
ISO/IEC 27005:2022(en) | |||
Information security, cybersecurity and privacy protection — Guidance on managing information security risks | |||
Table of contents | |||
Foreword | |||
Introduction | |||
1 Scope | |||
2 Normative references | |||
3 Terms and definitions | |||
3.1 Terms related to information security risk | |||
3.2 Terms related to information security risk management | |||
4 Structure of this document | |||
5 Information security risk management | |||
5.1 Information security risk management process | |||
5.2 Information security risk management cycles | |||
6 Context establishment | |||
6.1 Organizational considerations | |||
6.2 Identifying basic requirements of interested parties | |||
6.3 Applying risk assessment | |||
6.4 Establishing and maintaining information security risk criteria | |||
6.5 Choosing an appropriate method | |||
7 Information security risk assessment process | |||
7.1 General | |||
7.2 Identifying information security risks | |||
7.3 Analysing information security risks | |||
7.4 Evaluating the information security risks | |||
8 Information security risk treatment process | |||
8.1 General | |||
8.2 Selecting appropriate information security risk treatment options | |||
8.3 Determining all controls that are necessary to implement the information security risk treatment options | |||
8.4 Comparing the controls determined with those in ISO/IEC 27001:2022, Annex A | |||
8.5 Producing a Statement of Applicability | |||
8.6 Information security risk treatment plan | |||
9 Operation | |||
9.1 Performing information security risk assessment process | |||
9.2 Performing information security risk treatment process | |||
10 Leveraging related ISMS processes | |||
10.1 Context of the organization | |||
10.2 Leadership and commitment | |||
10.3 Communication and consultation | |||
10.4 Documented information | |||
10.5 Monitoring and review | |||
10.6 Management review | |||
10.7 Corrective action | |||
10.8 Continual improvement | |||
Annex A Examples of techniques in support of the risk assessment process | |||
A.1 Information security risk criteria | |||
A.2 Practical techniques | |||
Bibliography | |||
== ISO 27005 - Anhänge == | == ISO 27005 - Anhänge == | ||
{| class="wikitable options" | {| class="wikitable options" | ||
Version vom 30. Mai 2024, 21:18 Uhr
ISO/IEC 27005 – Information security risk management
Beschreibung
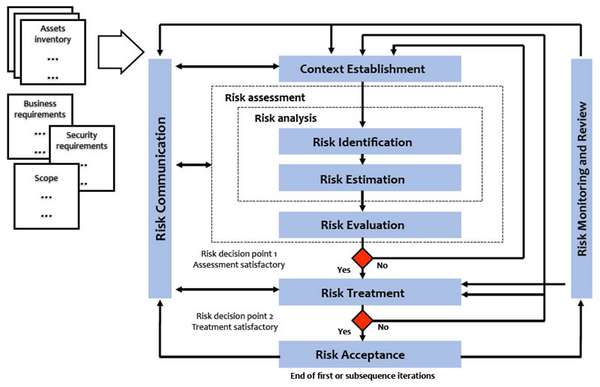
ISO 27005 behandelt das Thema IS Risikomanagement
- Prozess-Überblick
| Schritte | Beschreibung |
|---|---|
| Context Establishment | Rahmenbedingungen klären |
| Risk Identification | Risiken identifizieren |
| Risk Estimation | Risiken einschätzen |
| Risk Evaluation | Risiken bewerten |
| Risk Treatment | Risiken behandeln |
| Risk Acceptance | (Rest-) Risiken akzeptieren |
| Risk Monitoring and Review | Risikoüberwachung und -überprüfung |
| Risk Communication | Risikokommunikation |
Inhalte
ISO/IEC 27005:2022(en) Information security, cybersecurity and privacy protection — Guidance on managing information security risks
Table of contents
Foreword Introduction 1 Scope 2 Normative references 3 Terms and definitions 3.1 Terms related to information security risk 3.2 Terms related to information security risk management 4 Structure of this document 5 Information security risk management 5.1 Information security risk management process 5.2 Information security risk management cycles 6 Context establishment 6.1 Organizational considerations 6.2 Identifying basic requirements of interested parties 6.3 Applying risk assessment 6.4 Establishing and maintaining information security risk criteria 6.5 Choosing an appropriate method 7 Information security risk assessment process 7.1 General 7.2 Identifying information security risks 7.3 Analysing information security risks 7.4 Evaluating the information security risks 8 Information security risk treatment process 8.1 General 8.2 Selecting appropriate information security risk treatment options 8.3 Determining all controls that are necessary to implement the information security risk treatment options 8.4 Comparing the controls determined with those in ISO/IEC 27001:2022, Annex A 8.5 Producing a Statement of Applicability 8.6 Information security risk treatment plan 9 Operation 9.1 Performing information security risk assessment process 9.2 Performing information security risk treatment process 10 Leveraging related ISMS processes 10.1 Context of the organization 10.2 Leadership and commitment 10.3 Communication and consultation 10.4 Documented information 10.5 Monitoring and review 10.6 Management review 10.7 Corrective action 10.8 Continual improvement Annex A Examples of techniques in support of the risk assessment process A.1 Information security risk criteria A.2 Practical techniques Bibliography
ISO 27005 - Anhänge
| Anhang | Thema | Beschreibung |
|---|---|---|
| A | Geltungsbereich | Bestimmung
|
| B | Assets |
|
| C | Typische Bedrohungen | |
| D | Typische Schwachstellen | Methoden zur Schwachstellenbewertung |
| E | Bewertung | Informationssicherheitsrisiken |
| F | Einwirkungen für das IT-Risikomanagement |